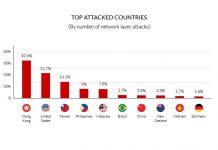
Q4 2017 Global DDoS Threat Landscape Report
Today we are releasing our latest Global DDoS Threat Landscape Report, a statistical analysis of 5,055 network and application layer DDoS attacks mitigated by...
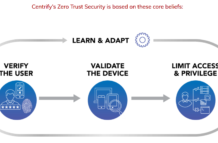
Six Reasons to Experience Zero Trust Security in Centrify Booth 501 at RSA
In case you hadn’t heard, the 2018 RSA Conference will be held April 16-19 at the Moscone Center in San Francisco. If you haven’t...
Closing the Integrity Gap with NIST’s Cybersecurity Framework
Closing the Integrity Gap with NIST's Cybersecurity Framework #outlook a{ padding:0; }...
Data Security Solutions for GDPR Compliance
Enforcement of the new EU General Data Protection Regulation (GDPR) adopted in 2016 starts on May 25, 2018. It requires all organizations that do...
Making Headlines: SAML
On February 27, 2018 the CERT Division of Carnegie Mellon University’s Software Engineering Institute issued advisory #475445, outlining a design flaw in Security Assertion...
Goodfellas, the Brazilian carding scene is after you
There are three ways of doing things in the malware business: the right way, the wrong way and the way Brazilians do it. From...
Centrify for NIST 800-171 MFA Compliance
I often speak with Federal System Integrators (FSIs) who need to implement Multi-Factor Authentication (MFA) as part of their NIST 800-171 compliance.
Specifically section 3.5.3...
OT Cybersecurity – Securing Your Industrial Operations for Reliability and Uptime
OT Cybersecurity - Securing Your Industrial Operations for Reliability and Uptime #outlook...
A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My...
As part of Imperva’s efforts to protect our customers’ data, we have an ongoing research project focused on analyzing and sharing different attack methods...







![[Part 4/4] Practical Advice to Network and Security Operations Pros Regarding GDPR Compliance](http://www.dataproof.co.za/wp-content/uploads/2018/04/part-4-4-practical-advice-to-network-and-security-operations-pros-regarding-gdpr-compliance-218x150.jpg)

![A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My Postgre Database to Start Mining Monero](http://www.dataproof.co.za/wp-content/uploads/2018/03/a-deep-dive-into-database-attacks-part-iii-why-scarlett-johanssons-picture-got-my-postgre-database-to-start-mining-monero-218x150.png)









