World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my...
Who’s who in the Zoo
ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation...
Configuring Imperva SecureSphere for GDPR Compliance: Part One
Time is running out. 23 days until GDPR enforcement
The GDPR effective date is less than a month away and, given the significant risk and...
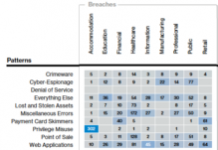
Insights from the Verizon 2018 Data Breach Investigation Report
The 2018 Verizon Data Breach Investigation Report (DBIR) was published in early April, reporting on 53,308 security incidents and 2,216 data breaches from 67...
Securing the Entire Container Stack, Lifecycle and Pipeline
Securing the Entire Container Stack, Lifecycle and Pipeline #outlook a{ padding:0; }...
DevSecOps Gathers More of the Spotlight at RSA 2018
Nearly 1,200 security professionals recently attended the DevOps Connect: DevSecOps Day at the 2018 RSA Conference at San Francisco’s Moscone Center.
Now in its fourth...
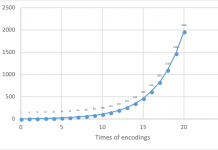
The Catch 22 of Base64: Attacker Dilemma from a Defender Point of View
Web application threats come in different shapes and sizes. These threats mostly stem from web application vulnerabilities, published daily by the vendors themselves or...
[Case Study] Delivering Security Needs On Time
Tripwire, Inc.









![[Case Study] Delivering Security Needs On Time](http://www.dataproof.co.za/wp-content/uploads/2018/04/case-study-delivering-security-needs-on-time.jpg)









