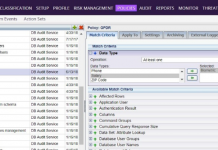
Monitoring Data & Data Access to Support Ongoing GDPR Compliance – Part III: Tools
The new European Union (EU)-wide General Data Protection Regulation (GDPR) was signed into law in late April 2016, and the compliance deadline came into...
LIVE BLOG: SecurIT Zero Trust Summit
REGISTER BELOW FOR THE LIVE STREAM!
Welcome to the live blog from SecurIT: the Zero Trust Summit for CIOs and CISOs.
SecurIT is an all-day...
Centrify Launches Zero Trust Security Network Ecosystem
The world has changed. I’m not sure if it was the HBO breach, Equifax, Yahoo, or one of the many breaches since, but after...
LuckyMouse hits national data center to organize country-level waterholing campaign
What happened?
In March 2018 we detected an ongoing campaign targeting a national data center in the Central Asia that we believe has been active...
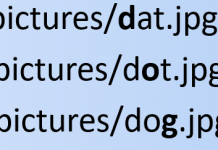
Clustering App Attacks with Machine Learning (Part 2): Calculating Distance
In our previous post in this series we discussed our motivation to cluster attacks on apps, the data we used and how we enriched...
DevOps Buyer’s Guide
DevOps Buyer's Guide #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{...
Five Reasons to Kill Off the Password
Australia recognised the security problem posed by passwords through widespread media coverage of Centrify’s warning issued on World Password Day, which occurred on May...
451 Research: Centrify Goes “All In” on the Zero Trust Movement
451 Research recently published an impact report recognizing Centrify as one of the early vendors to embrace the Zero Trust concept, which is a...
Map Your Security Controls to an Established Framework
Tripwire, Inc.