Gemalto shares will be delisted on 29 May 2019
- Read more
Casino Goes All In and Wins Big with Imperva Security
There’s no good time to be hit by ransom-seeking DDoS attackers. For one casino-entertainment provider, the timing was particularly bad — right before one...
How to Migrate to the Cloud Without Compromising Your Security Posture
How to Migrate to the Cloud Without Compromising Your Security Posture #outlook...
New zero-day vulnerability CVE-2019-0859 in win32k.sys
In March 2019, our automatic Exploit Prevention (EP) systems detected an attempt to exploit a vulnerability in the Microsoft Windows operating system. Further analysis...
[Case Study] Securing Your Data In The Cloud
Tripwire, Inc.
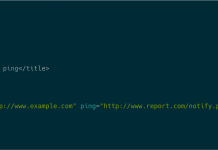
The Ping is the Thing: Popular HTML5 Feature Used to Trick Chinese Mobile Users...
DDoS attacks have always been a major threat to network infrastructure and web applications.
Attackers are always creating new ways to exploit legitimate services...
Large-scale SIM swap fraud
Introduction
SIM swap fraud is a type of account takeover fraud that generally targets a weakness in two-factor authentication and two-step verification, where the second...
Gaza Cybergang Group1, operation SneakyPastes
Gaza Cybergang(s) is a politically motivated Arabic-language cyberthreat actor, actively targeting the MENA (Middle East North Africa) region, especially the Palestinian Territories.
The confusion surrounding...
Project TajMahal – a sophisticated new APT framework
Executive summary
‘TajMahal’ is a previously unknown and technically sophisticated APT framework discovered by Kaspersky Lab in the autumn of 2018. This full-blown spying framework...
The Industrial Control System Visibility Imperative
The Industrial Control System Visibility Imperative #outlook a{ padding:0; } body{ width:100%...






![[Case Study] Securing Your Data In The Cloud](http://www.dataproof.co.za/wp-content/uploads/2019/04/case-study-securing-your-data-in-the-cloud.jpg)