According to Gartner, companies will spend up to $96 billion worldwide on security this year, but research by Centrify and Dow Jones suggests that up to 79% of companies have experienced a significant breach.
Forrester estimates that 80% of security breaches involve privileged credentials. It’s understandable: After an intruder gains access to the employees’ devices, they try to snoop the network and install keylogger to get higher privilege credentials (such as root or administrator). Privileged credentials provide greater scope for stealing data en masse than individual accounts do.
Traditional Privileged Access Management (PAM) products have been trying to resolve the problem by either leveraging the privilege elevation policy or vault account with high risk entitlements. These solutions often rely on administrators to setup the static rules to secure or audit the privileged accounts, which creates numerous blind spots e.g. unknown privilege entitlements, excessive privilege abuse, improper policy setup etc.
AI AND MACHINE LEARNING TO THE RESCUE
Artificial Intelligence systems which are designed to learn and adapt are capable of perceiving miniscule moves in online undercurrents. They are much more capable than humans when it comes to identifying the blind spots, protecting privileged accounts, detecting cyber threat, responding to the ongoing threat and providing the recovery solution.
AI is the answer to the traditional rule- and policy-based control type of security that is no longer effective, especially in the context of PAM. AI can secure the enterprises networks against the unknown, as opposed to the traditional solutions that can only protect against the known.
Centrify Analytics Service (CAS), a multi-tenant cloud service, is applying AI and big data analytics to offer intelligent, real-time access security so that improper security policy, unnecessary permission and access anomaly can be eliminated or detected for monitoring with User Entity Behavior Analytics. It creates a baseline to understand a user or entity’s behavior on a regular basis.
Administrators can explore this data to understand how the privileged account is being used via various tools that CAS provides. Meanwhile, CAS automatically assesses risk based on constantly-evolving user, endpoint, application and infrastructure behavior patterns. Once the user and/or entity behavior begins to deviate from its normal behavior, it then assigns a risk score, enforces an appropriate access decision, and adaptively collects additional audit data (e.g. session recording) using advanced real-time machine learning algorithms.
NEW PUBLIC SECTOR REQUIREMENTS

The NIST Cybersecurity Framework (CSF) is U.S. Government guidance for private sector organizations that own, operate, or supply critical infrastructure. It establishes basic processes and essential controls for cybersecurity.
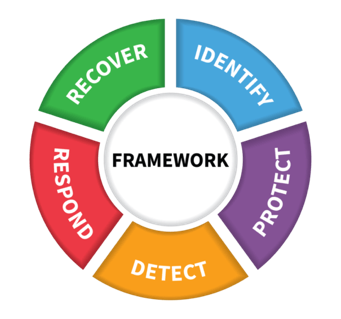
CSF consists of five concurrent and continuous Core Functions: Identify, Protect, Detect, Respond and Recover. On May 11, 2017, the presidential executive order on strengthening cybersecurity of federal networks and critical infrastructure was issued which explicitly mandates that federal agencies should implement the Cybersecurity Framework (CSF). According to Gartner, by 2020, more than 50% of organizations will use the NIST Cybersecurity Framework, up from the current 30% in 2015.
IDENTIFY, PROTECT, DETECT, RESPOND & RECOVER

Centrify Analytics Service uses the five core functions of CSF as the key reference points, and provides a strategic view of the lifecycle of an organization’s cybersecurity risk management. The service can also help organization to address most of the CSF controls and metrics related to privileged access management. The near real-time insights and controls, which are provided to IT security professionals, auditors and executives, can be categorized into the following:
1. Identify

Centrify Analytics Service collects not only the time series event of all access and activity of all users but also the versioned access entitlement models (also referred to as “authorizations,” “privileges,” “access rights,” “permissions,” “rules,” and/or “policies”). By cross-referencing time series event data and model data such as access entitlements, CAS can be used to identify full contextual function areas such as asset management and risk management. For example:
- Built-in dashboards provide 360 degree view of identity and access with details one click away.
- Discover the identity and access risks, e.g. excessive, inappropriate and unused privileges, who setup the risk entitlement, user run as local admin, etc.
- Discover user effective rights on computers
- Discover the access entitlement changes
- Discover the domain admin effective rights
- Discover the active local root/admin accounts
- Discover the stealth servers
- Discover the local privileged account activity patterns

2. Protect
 Instead of relying on hardcoded rules, Centrify Analytics Service produces risk score for any access attempts (e.g. login, privilege elevation, command usage, application usage etc.) by leveraging machine learning. The risk-based access policies can be setup to stop anomalous activity in real time – at the point of access.
Instead of relying on hardcoded rules, Centrify Analytics Service produces risk score for any access attempts (e.g. login, privilege elevation, command usage, application usage etc.) by leveraging machine learning. The risk-based access policies can be setup to stop anomalous activity in real time – at the point of access.
Since access control decisions are made based on risk level, Centrify Analytics Service can be easily created to:

- Ease low-risk access for typical access requests
- Prompt MFA when requests are outside of typical user behavior
- Block access entirely for requests that present high risk
3. Detect
Centrify Analytics Service continually monitors the near real-time event stream and detects the anomalous behavior and potential threats with a threat detection engine. This engine uses big data analytics and real-time machine learning algorithms to automatically identify the risks from the massive amount of access event data and access entitlements data.
Once a threat is detected, it annotates the risky event with risk score as well as the risk distribution and create an alert. Meanwhile, CAS learns and updates the user/entity behavior profile based on the real-time event stream that it scans through.
CAS-enabled security teams to see the system access, anomaly detection in high resolutions with analytics tools such dashboards, explorer views, and investigation tools.
To illustrate a typical threat monitoring and investigation flow:
- Administrator starts with “Threat Monitoring” built-in dashboard
- Drills down into “Threat Monitoring” explorer view and review the risk and risk distribution.
- Selects an alert and investigates in “Session Timeline” tool
- Replays the recorded session view

4. Respond
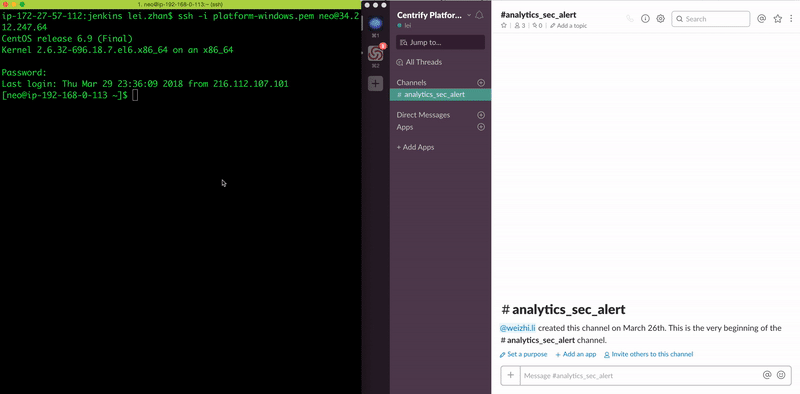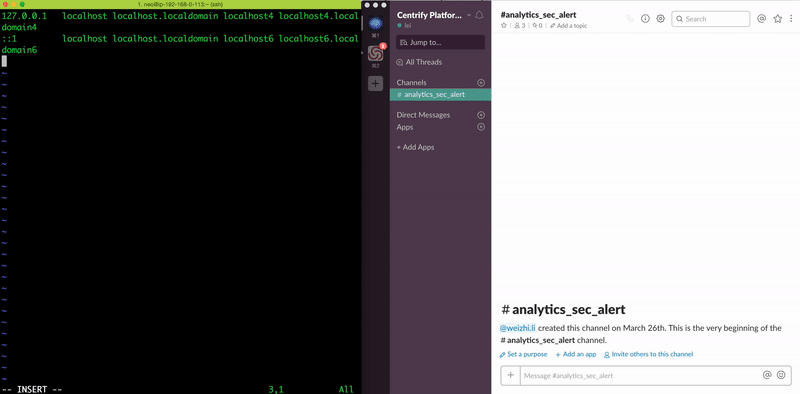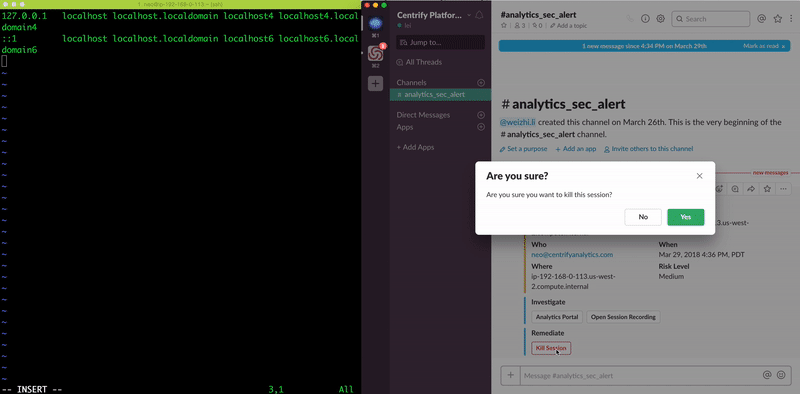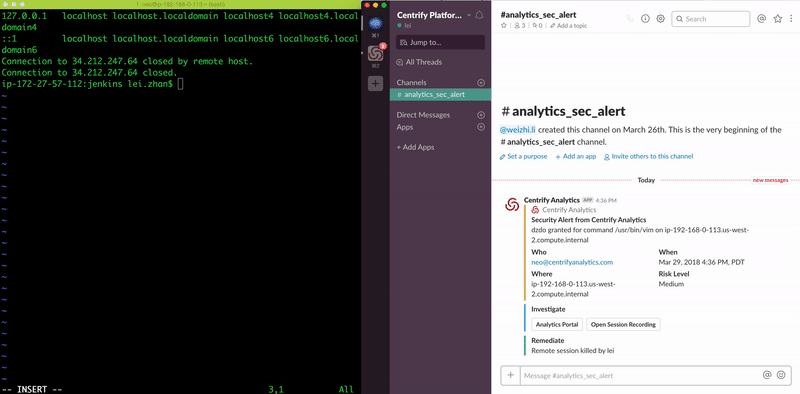
Should an alert event occur, Centrify Analytics Service allows the user to easily fire off alerts from CAS into third-party applications via webhook. This capability enables user to response to a threat alert and contain the impact with following means:
- Notification: PagerDuty, Slack, SMS
- Mitigation: Manually or automatically terminate a session based on the risk
- Integration: Feed event/alert from CAS to the third-party system, e.g. trigger a ServiceNow automation or workflow, forward alert to SIEM etc.
- Automation and Orchestration: Trigger a custom automation by leveraging server-less frameworks e.g. kill the session by using AWS Step Functions or AWS Lambda.
Centrify Analytics Service can not only stream events and create snapshot entitlement model from Centrify products family, but also from third-party security tools. The machine learning-powered threat detection engine can cross reference the data from different sources to enhance its inference capability. The rich analytics toolset also allows a user to perform additional analysis and forensics.
5. Recover
Centrify Analytics Service continuously monitors and learns from the data it collects from various data sources and, based on the historical data, it can provide a user role assignment recommendation based on the least privilege model.

“Poorly managed privileged access can expose organizations to security breaches and regulatory rebukes, resulting in business losses and financial penalties. Security and risk management leaders must effectively manage privileged access in a risk-aware fashion,” per a Gartner summary for its 2017 Best Practices for Privileged Access Management report.
It is pretty obvious that the emergence of risk aware security products powered by Machine Learning, Artificial Intelligence and Big Data technologies will quickly become the de facto standard weapon for enterprises to fight against security breaches. That starts with understanding risk through real-time analytics, such as Centrify Analytics Service.
The post Stop Breaches with Analytics and Artificial Intelligence appeared first on Secure Thinking by Centrify.