Lexi DiScola’s guide to global teamwork and overflowing TBRs
Welcome back to Humans of Talos. This month, Amy chats with Senior Cyber Threat Analyst Lexi DiScola from the Strategic Analysis team. Lexi’s journey into cybersecurity is anything but traditional — she brings a background in political science and French to her work tracking global cyber threats and collaborating with colleagues across continents.Tune in as Lexi opens up about...
Security by Design: Why Multi-Factor Authentication Matters More Than Ever
In an era marked by escalating cyber threats and evolving risk landscapes, organisations face mounting pressure to strengthen their security posture whilst maintaining seamless user experiences. At Thales, we recognise that robust security must be foundational – embedded into products and services by design, not bolted on as an afterthought. This principle underpins our commitment to the U.S. Cybersecurity...
Windows Persistence Explained: Techniques, Risks, and What Defenders Should Know
By: Kahng An, Intelligence TeamModern Windows systems include many built-in features that help applications run smoothly and support everyday user activity. Unfortunately, many of these built-in functionalities can be exploited by threat actors in order to have malware payloads remain on a system and run without user interaction. These different features can be abused to be what security researchers...
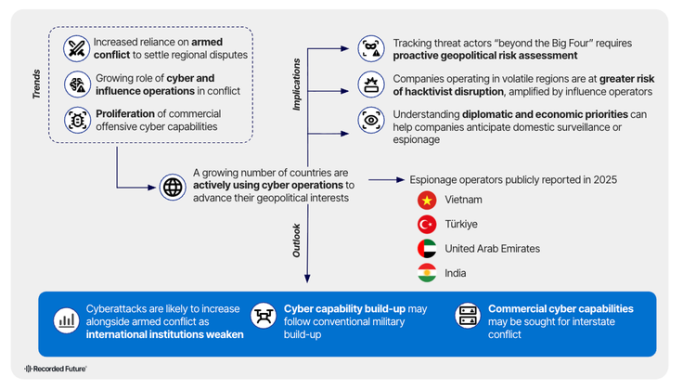
Cyber on the Geopolitical, Battlefield: Beyond the, “Big Fourˮ
Executive Summary Regional conflicts and weakened international institutions are driving the use of offensive cyber operations beyond the “Big Four” (China, Russia, Iran, and North Korea). Monitoring these threat actors requires organizations to proactively assess their geopolitical risk to understand where future threats are most likely to emerge. In 2025, Recorded Future identified at least twenty actors across...
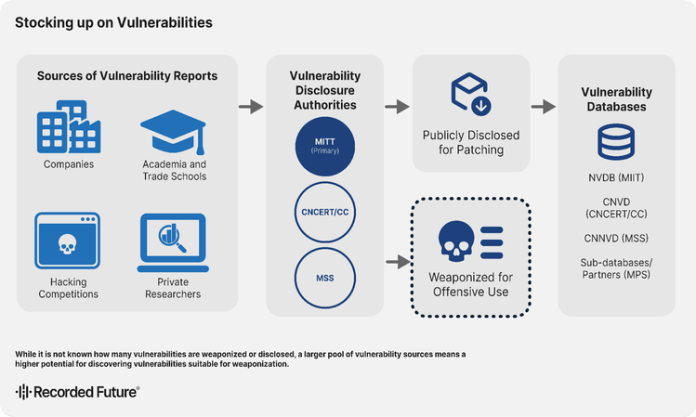
China’s Zero-Day Pipeline: From Discovery to Deployment
Executive Summary China’s observed use of zero-days has declined since 2023. However, it has expanded its capacity to discover and manage vulnerabilities, signaling a continued effort toward stockpiling exploits for strategic or military advantage. The Data Security Law (DSL) and Provisions on the Management of Network Product Security Vulnerabilities (RMSV) give the Chinese state first access and...
The $0 Transaction That Signaled a Nation-State Cyberattack
Key Points: Fraud enables cyber operations: Threat actors used compromised payment cards validated through Chinese-operated card-testing services to attempt unauthorized access to Anthropic's AI platform during a reported state-sponsored espionage campaign. Card testing signals downstream attacks: The observed fraud followed a predictable kill chain—compromise, validation, resale, and attempted cashout—providing early warning indicators that preceded...
BlueDelta’s Persistent Campaign Against UKR.NET
The analysis cut-off date for this report was July 30, 2025 Executive Summary Between June 2024 and April 2025, Recorded Future’s Insikt Group identified a sustained credential-harvesting campaign targeting users of UKR.NET, a widely used Ukrainian webmail and news service. The activity is attributed to the Russian state-sponsored threat group BlueDelta (also known as APT28, Fancy Bear, and...
Introducing Pathfinding.cloud
Introducing Pathfinding.cloud, a library of AWS IAM privilege escalation paths - Read more
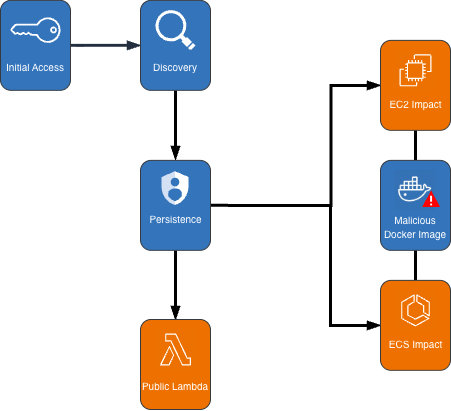
GuardDuty Extended Threat Detection uncovers cryptomining campaign on Amazon EC2 and Amazon ECS
Amazon GuardDuty and our automated security monitoring systems identified an ongoing cryptocurrency (crypto) mining campaign beginning on November 2, 2025. The operation uses compromised AWS Identity and Access Management (IAM) credentials to target Amazon Elastic Container Service (Amazon ECS) and Amazon Elastic Compute Cloud (Amazon EC2). GuardDuty Extended Threat Detection was able to correlate signals across these...
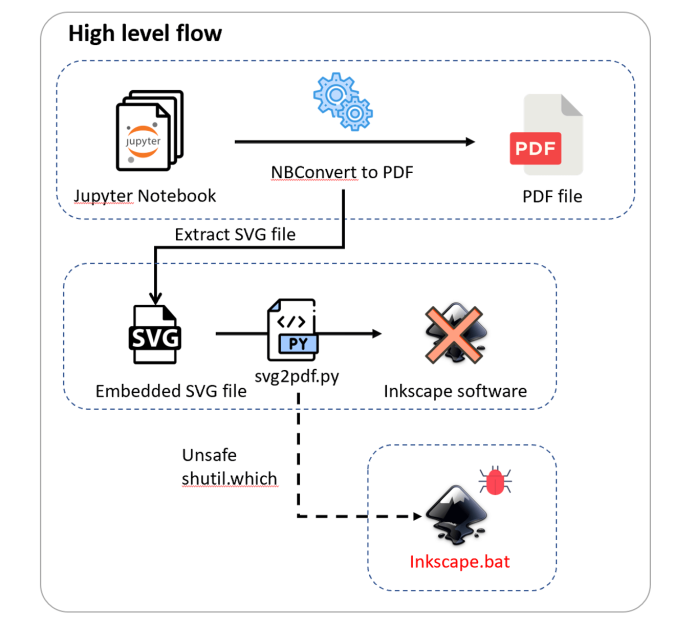
Code Execution in Jupyter Notebook Exports
After our research on Cursor, in the context of developer-ecosystem security, we turn our attention to the Jupyter ecosystem. We expose security risks we identified in the notebook’s export functionality, in the default Windows environment, to help organizations better protect their assets and networks.
Executive Summary
We identified a new way external Jupyter notebooks could be exploited by threat actors...