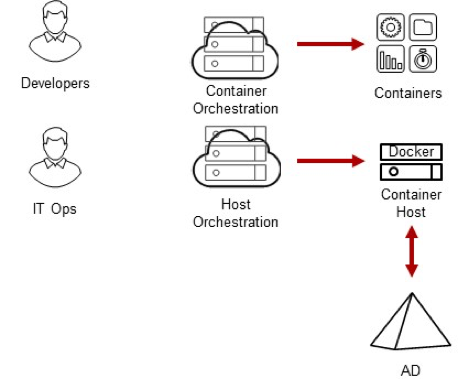
Centrify Identity Services: Securing Docker and Containers
Introduction
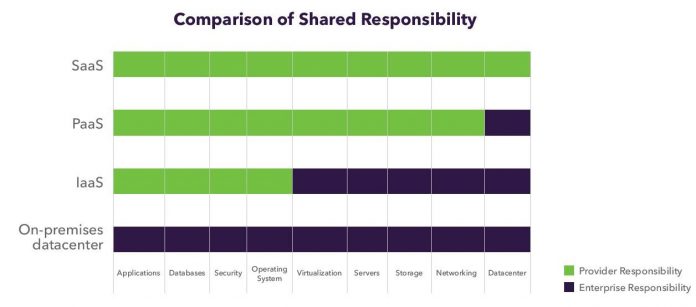
We are excited to announce that Centrify now supports CoreOS Container Optimized Linux which several of our customers are using as part of their adoption of containerization for their application deployments. But first, let’s start with an overview of how Centrify can help you protect access to these containerized platforms and the applications that run on them.
As organizations embrace...
Cloud Database Migration Peer Insights [Report]
Not long ago, for security, compliance or other reasons, it was unthinkable for many regulated organizations to move sensitive data into the cloud. It’s striking how things have changed.
Maybe it was inevitable that services like email were cloud migration candidates. People trust Microsoft, and it’s quite impressive what they have done to make Office 365 simple to adopt and...
4 Steps to Reduce the Risk of Shared Account Passwords
Reduce the Risk of a Security Breach When Sharing Privileged Accounts
There are partners, employees, contractors, customers and others who access or try to access your most valuable company assets on a daily basis. But each individual or each group represents a high risk if their privileges are not managed properly. Time and time again we see an employee or...
KLAS Findings on Healthcare DLP Strategies
KLAS Findings on Healthcare DLP Strategies
This webinar was recorded on December 19, 2017.
- Read more
Cloud Migration Fundamentals
The advantages offered by a cloud-based environment make it an easy decision for most companies to make. Still, there are numerous critical choices to be made that can transform the complexities of the migration process into a relatively smooth transition—especially regarding application and data security.
This article describes the options available to you when you are planning a migration of...
Centrify Predicts: Cybersecurity in 2018
As we start 2018, we have continued to see major breaches across industries, only last year we witnessed at least two companies — Uber and Equifax — opt to hold off on alerting the public to their respective cybersecurity breaches and make them public at a later, more convenient date. Whether a coincidence or a trend in the making,...
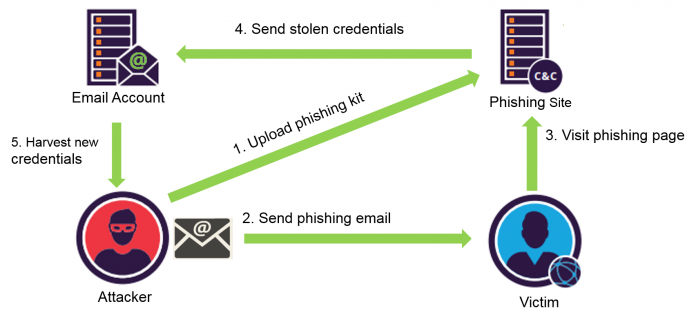
Our Analysis of 1,019 Phishing Kits
In recent years phishing activity has grown rapidly, with thousands of phishing sites popping for a virtual moment that last weeks, days or even hours, before becoming ineffective—either getting blacklisted by security providers, or brought down by internet providers and authorities, or (in most cases) both. In order to keep up with this dynamic, a significant portion of the...
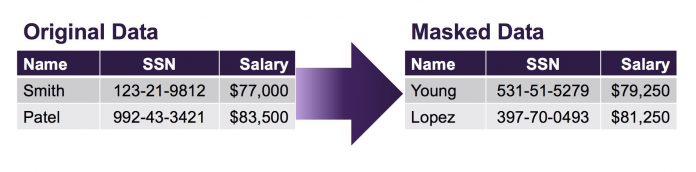
Three Reasons Why GDPR Encourages Pseudonymization
The General Data Protection Regulation (GDPR) is the European Union’s new data regulation designed to provide individuals with rights and protections over their personal data that is collected or created by businesses or government entities. It unifies data protection regulation across all member states of the European Union (EU) and is set to replace the Data Protection Directive. The...
Centrify Joins FIDO Alliance and Expands Partnership with Yubico
Centrify has been busy building innovative technology and powerful partnerships. This post will talk about a longtime partnership, cool tech, and a deeper level of integration. Centrify and Yubico have been partners for more than three years already and work together with joint customers, in the field, and at a corporate level.
Centrify and Yubico U2F Integration
To further its move...
The Year in Review: Centrify Builds Momentum
The Centrify solution made great strides in 2017, chronicled in Part I of this blog. Product enhancements, combined with the market’s growing understanding of the essential role identity plays in effective cybersecurity propelled the business forward. Here are some additional business highlights:
The Centrify/Ponemon study
Early in 2017, Centrify sponsored a Ponemon research study
to discover the business and financial impact of...

![Cloud Database Migration Peer Insights [Report]](https://www.dataproof.co.za/wp-content/uploads/2018/01/cloud-database-migration-peer-insights-report.png)