Home Blog
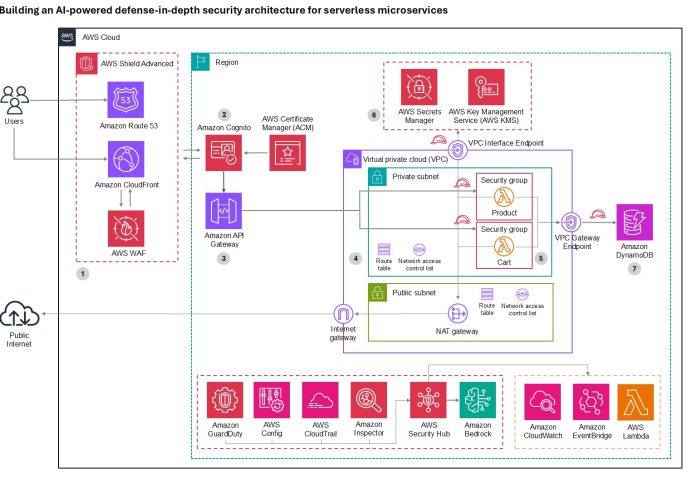
Building an AI-powered defense-in-depth security architecture for serverless microservices
Enterprise customers face an unprecedented security landscape where sophisticated cyber threats use artificial intelligence to identify vulnerabilities, automate attacks, and evade detection at machine speed. Traditional perimeter-based security models are insufficient when adversaries can analyze millions of attack vectors in seconds and exploit zero-day vulnerabilities before patches are available. The distributed nature of serverless architectures compounds this...
Fake CAPTCHA Scam Tricks Windows Users Into Installing Malware
A fake CAPTCHA scam is tricking Windows users into running PowerShell commands that install StealC malware and steal passwords, crypto wallets, and more.
The post Fake CAPTCHA Scam Tricks Windows Users Into Installing Malware appeared first on TechRepublic. - Read more
16th February – Threat Intelligence Report
For the latest discoveries in cyber research for the week of 16th February, please download our Threat Intelligence Bulletin.
TOP ATTACKS AND BREACHES
Dutch telecom provider Odido was hit by a data breach following unauthorized access to its customer management system. Attackers extracted personal data of 6.2 million customers, including names, addresses, phone numbers, email addresses, bank account details, dates of...
Vulnerabilities in Password Managers Allow Hackers to View and Change Passwords
Security researchers have challenged end-to-end encryption claims from popular commercial password managers - Read more
Nanobot Unauthenticated WhatsApp Session Hijack via WebSocket Bridge
Nanobot Unauthenticated WhatsApp Session Hijack via WebSocket Bridge Tenable Research has identified and responsibly disclosed a vulnerability to Nanobot.The nanobot WhatsApp bridge server (`bridge/src/server.ts`) binds its WebSocket server to all network interfaces (`0.0.0.0`) and accepts connections without any form of authentication. An attacker with network access to the bridge port (default `3001`) can fully hijack the linked WhatsApp session:...
APOIA.se – 450,764 breached accounts
In December 2025, a database of the Brazilian crowdfunding platform APOIA.se was posted to an online forum. In January 2026, the company confirmed it had suffered a data breach. The incident exposed 451k unique email addresses along with names and physical addresses. - Read more
Making sense of AI’s role in cyber security
Cyber security companies have jumped on the AI bandwagon. We look at where artificial intelligence is a useful add-on and where it poses potential risks - Read more
Windows 11 KB5077181 Security Update Causing Some Devices to Restart in an Infinite Loop
Microsoft’s February 10, 2026, security update KB5077181 for Windows 11 versions 24H2 (build 26200.7840) and 25H2 (build 26100.7840) has triggered widespread reports of critical boot failures just days after deployment. Users describe devices entering infinite restart loops, often exceeding 15 cycles, preventing access to the desktop. This cumulative update delivers essential security fixes alongside quality improvements from prior releases...
Viral AI Caricatures Highlight Shadow AI Dangers
A viral AI caricature trend may be exposing sensitive enterprise data, fueling shadow AI risks, social engineering attacks, and LLM account compromise.
The post Viral AI Caricatures Highlight Shadow AI Dangers appeared first on TechRepublic. - Read more
Critical BeyondTrust RS vulnerability exploited in active attacks
Researchers warn that a critical vulnerability patched this week in BeyondTrust Remote Support is being exploited in the wild to compromise self-hosted deployments, including Bomgar remote support appliances, which included affected versions of the impacted software. Bomgar, a provider of privileged identity and access management products, acquired BeyondTrust in 2018, adopting the latter’s brand name....