Network Intelligence: Your Questions, Global Answers
The Problem with Pre-Packaged Intelligence Security teams are drowning in threat intelligence feeds. Hundreds of vendors promise comprehensive coverage, real-time alerts, and actionable...
State of Security Report | Recorded Future
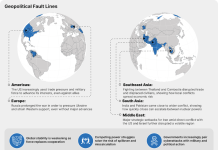
Fragmentation is the new normal The global threat landscape didn't simplify in 2025—it shattered. Geopolitical alliances strained. Criminal enterprises splintered...
Fragmentation Defined 2025’s Threat Landscape. Here’s What It Means for 2026
Uncertainty has become the operating environment for business. And this year, fragmentation is driving it. The global threat landscape didn't simplify in 2025;...
From 27 Steps to 5: How Recorded Future Reimagined Threat Hunting with Autonomous Threat...
The manual operations gap can be a business risk Manual threat hunting requires 27 steps that burn analyst time...
Rublevka Team: Anatomy of a Russian Crypto Drainer Operation
Executive Summary Insikt Group has identified a major cybercriminal operation specializing in large-scale cryptocurrency theft, operating under the moniker “Rublevka Team”. Since its...
Autonomous Threat Operations in action: Real results from Recorded Future’s own SOC team |...
Key Takeaways: Recorded Future deployed Autonomous Threat Operations within its own SOC before customer release, ensuring real-world effectiveness and identifying critical capabilities....
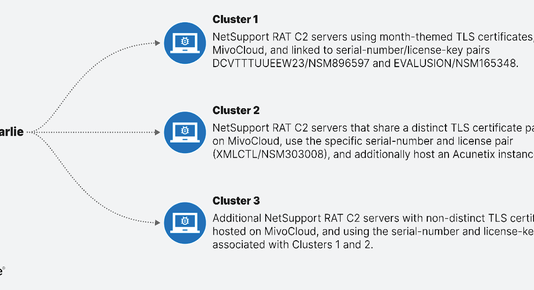
PurpleBravo’s Targeting of the IT Software Supply Chain
Executive Summary PurpleBravo is a North Korean state-sponsored threat group that overlaps with the “Contagious Interview” campaign first documented in November 2023. It...
Threat and Vulnerability Management in 2026
Key Takeaways: Traditional vulnerability management tools can no longer keep up with the speed of modern exploitation—threat context is now mandatory. Threat...
Best Ransomware Detection Tools
Key Takeaways Effective ransomware detection requires three complementary layers: endpoint and extended detection and response (EDR/XDR) to monitor device-level activity, network detection...
December 2025 CVE Landscape: 22 Critical Vulnerabilities Mark 120% Surge, React2Shell Dominates Threat Activity
December 2025 witnessed a dramatic 120% increase in high-impact vulnerabilities, with Recorded Future's Insikt Group® identifying 22 vulnerabilities requiring immediate remediation, up from...