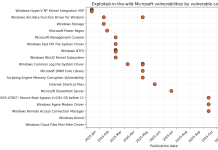
Check Point Research continuously investigates real-world attacks, vulnerabilities, attackers’ infrastructure, and emerging techniques across global networks and environments. The Cyber Security Report 2026 consolidates our research efforts throughout 2025 to deliver a clear, data-driven view of the current threat landscape and its trajectory in 2026.
As Check Point’s flagship annual research publication, the report serves as a reference point for security teams, researchers, and industry leaders seeking to understand how attacker behavior is evolving in practice, not just theory. The findings below highlight the most significant shifts shaping the threat landscape today.
AI as a Force Multiplier Across Cyber Attacks
Artificial intelligence is now embedded across the attack lifecycle, accelerating the execution of familiar techniques at greater speed and scale.
Key observations:
- Increasingly convincing social engineering with fewer detectable indicators
- Faster reconnaissance and targeting, reducing time-to-compromise
- Accelerated malware development
Alongside its role as an enabler, AI is now a direct source of enterprise risk. Research in 2025 identified measurable exposure tied to how organizations deploy and govern AI systems.
Key data points:
- Risky AI prompts increased by 97% in 2025
- 40% of analyzed Model Context Protocols (MCPs) were vulnerable
- Elevated trust and autonomy amplify the impact of prompt injection and workflow abuse
Similar efficiency-driven patterns were also observed in financially motivated operations, including ransomware activity.
Ransomware Operations Become More Fragmented and Targeted
Ransomware activity continued to increase in 2025, despite multiple law enforcement takedowns of high-profile groups.
Research findings show:
- A shift away from centralized ransomware brands toward smaller, decentralized operators
- Increased use of data-only extortion without encryption
- More personalized extortion tactics based on victim profiling
- Shorter attack and negotiation timelines supported by automation and AI
This evolution reflects a shift toward operational efficiency and decentralized execution.
Unmonitored Devices as High-Value Initial Access Targets
Unmonitored devices played a growing role in intrusion activity, particularly in large-scale and targeted attacks.
Observed trends include:
- Exploitation of routers, gateways, VPN appliances, and other perimeter devices
- Use of edge devices for persistent access and lateral movement
- Delayed detection due to limited monitoring and patching coverage
- Supply-chain and vendor ecosystem exposure amplifying risk
These devices often sit outside standard endpoint and identity security controls.
Cyber Activity Aligns More Closely With Geopolitical Conflicts
Threat activity in 2025 increasingly mirrored real-world geopolitical tensions, with cyber operations synchronized to physical and political events.
Key characteristics include:
- Coordination between cyber espionage, disruption, and influence campaigns
- Targeting of infrastructure and information systems linked to regional conflicts
- Use of compromised IoT and surveillance systems to support physical-world operations
This convergence complicates attribution, as activity may involve overlapping criminal and state-aligned characteristics.
Common Pattern: Speed, Scale, and Reduced Visibility
Across all major trends, researchers observed consistent patterns in attacker operations:
- Faster execution cycles
- Broader targeting with fewer resources
- Reduced reliance on custom tooling
Chinese-Nexus Cyber Threats
During 2025 the Chinese-nexus activity was global by design:
- Operations are industrialized, not opportunistic
- Edge and perimeter infrastructure as primary foothold
- Routine zero-day and rapid one-day weaponization
What Security Teams Are Seeing in Practice
Based on activity observed throughout 2025, researchers identified the following conditions present across multiple environments:
- Continuous exposure created by misconfigurations, identity weaknesses, and unmanaged assets
- Increased reliance on identity-based access paths in intrusion activity
- Measurable risk introduced by ungoverned AI usage
- Attack paths spanning cloud, edge, SaaS, and on-prem environments
Conclusion
The findings in the Cyber Security Report 2026 reflect sustained observation of real-world attacker behavior rather than isolated incidents or short-term trends. By correlating telemetry, vulnerability research, and active threat investigations across regions and sectors, the report documents how attacker behavior and infrastructure evolved during 2025.
As a long-running, data-driven research publication, the report is intended to support informed analysis, planning, and discussion across the security community, from practitioners and researchers to decision-makers responsible for managing risk in 2026 and beyond.
Read the Cyber Security Report 2026
Access the full report to explore the underlying data, research methodology, and detailed analysis behind these findings.
The post Cyber Security Report 2026 appeared first on Check Point Research.