Holiday shopping season is in full swing, and Black Friday 2025 continued to demonstrate that consumer demand and attacker activity shows no signs of slowing. According to Adobe Analytics, U.S. consumers spent $11.8 billion online on Black Friday, setting a new record and highlighting sustained strength in online shopping. Yet behind this surge in legitimate traffic, retailers also faced a sharp rise in automated abuse, account takeover attempts, and reconnaissance across their digital storefronts.
This post breaks down what we saw across our network during the Black Friday period, including traffic trends, attack behavior, targeted geographies, and insights retailers can apply to strengthen their defenses ahead of the holiday home stretch.
What We Saw
Massive Traffic Surges Extending Past Black Friday
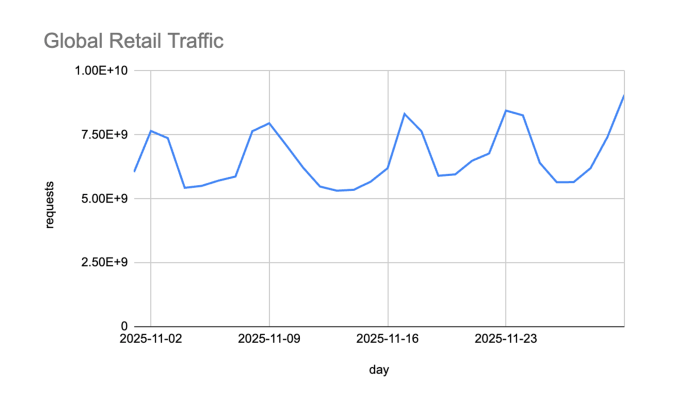
Retail traffic surged 37% above November averages, peaking on Black Friday but continuing into the weekend of November 29–30. Traditionally, traffic dips slightly on Saturday before building again on Cyber Monday, but this year showed a clear shift: shoppers kept buying throughout the weekend. This aligns with broader retail trends showing consumers taking advantage of longer promotional windows rather than concentrating purchases on a single day.
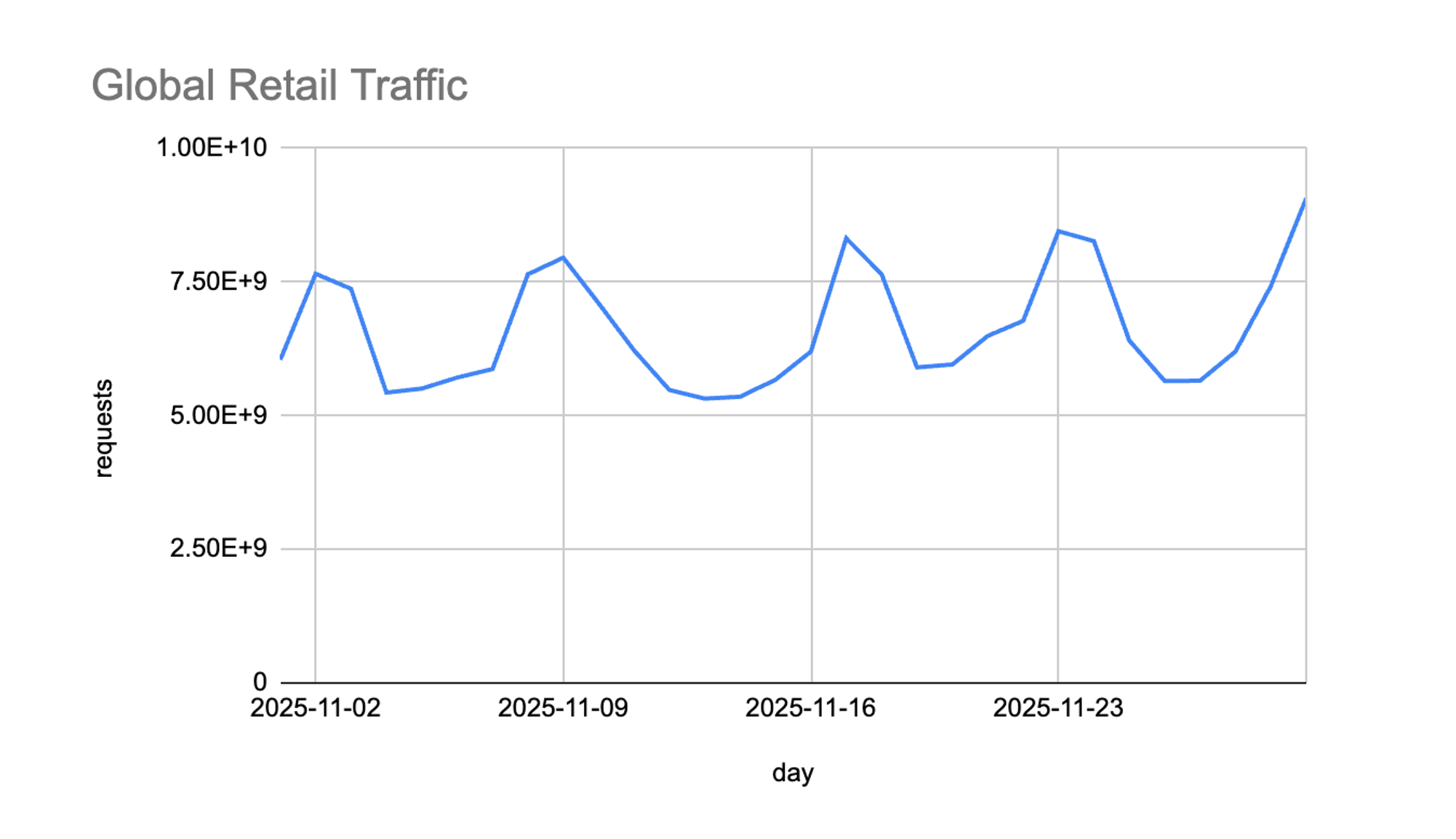
For retailers, this means the “peak” period is expanding- and with it, the window of exposure to cyber threats.
Bot Attacks Rose 50%, Focused on High-Value Workflows
Alongside legitimate traffic, bot attacks on retail sites spiked 50% over the November average. The timing closely tracked promotional activity, suggesting attackers were attempting to exploit increased consumer volume to blend in and avoid detection.
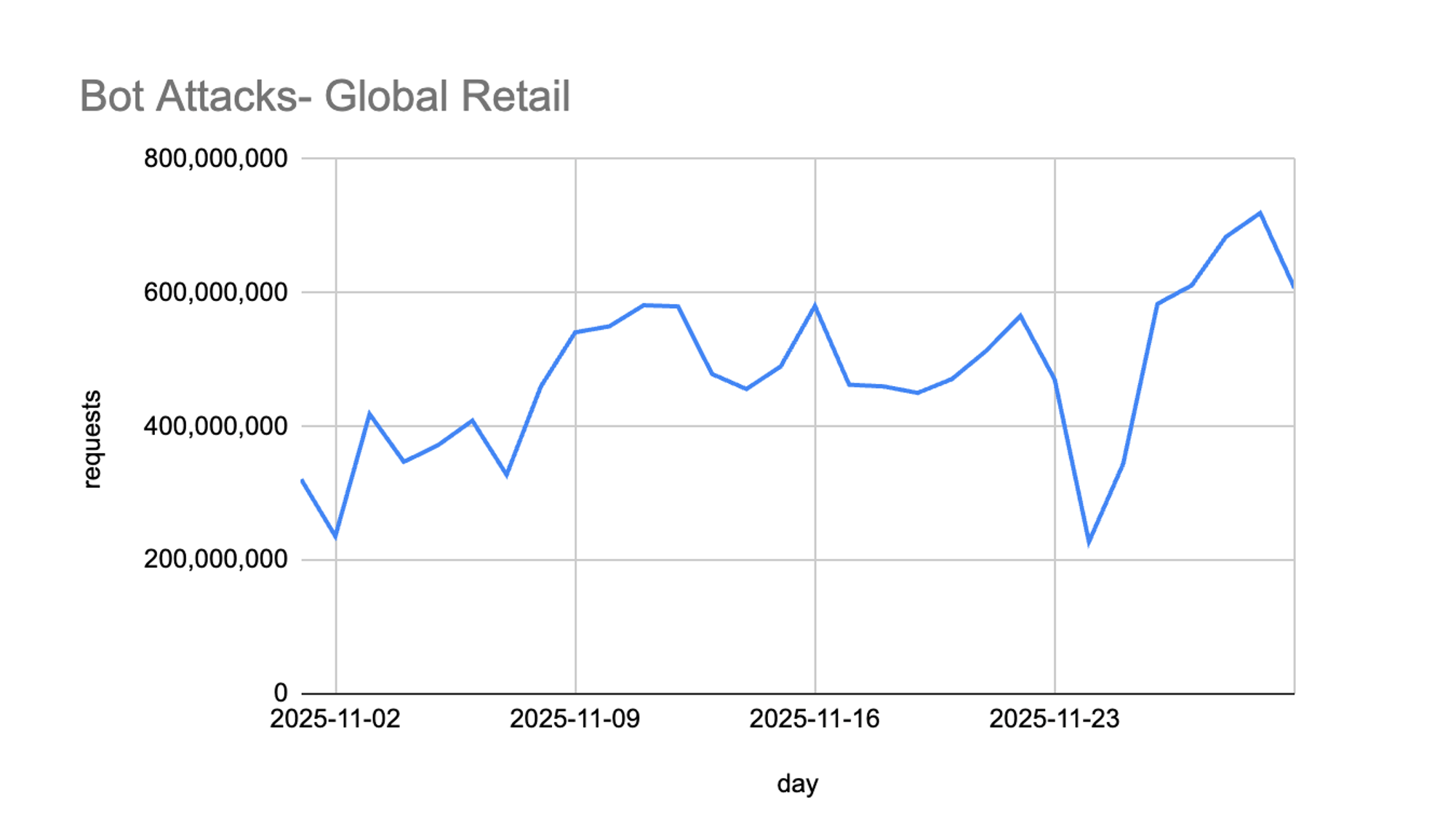
Broadly, these bots targeted:
- Authentication and account flows (e.g., /login)
- Inventory and product data endpoints (e.g., /datastore, /event/)
- Transaction and application paths (e.g., credit-card application flows, lottery/promotion services, and user log endpoints)
This behavior reflects typical seasonal abuse campaigns: credential stuffing to hijack accounts, automated scraping to gain pricing or inventory intelligence, and attempts to manipulate promotions or loyalty flows.
Attacks Concentrated on the US, UK, and Australia
Malicious traffic during Black Friday was heavily concentrated in three markets: the US (46%), Australia (12%), and the UK (11%). These regions represent some of the world’s most active e-commerce ecosystems, and attackers mirrored legitimate consumer behavior by focusing on markets with the highest transaction volumes and promotional activity.
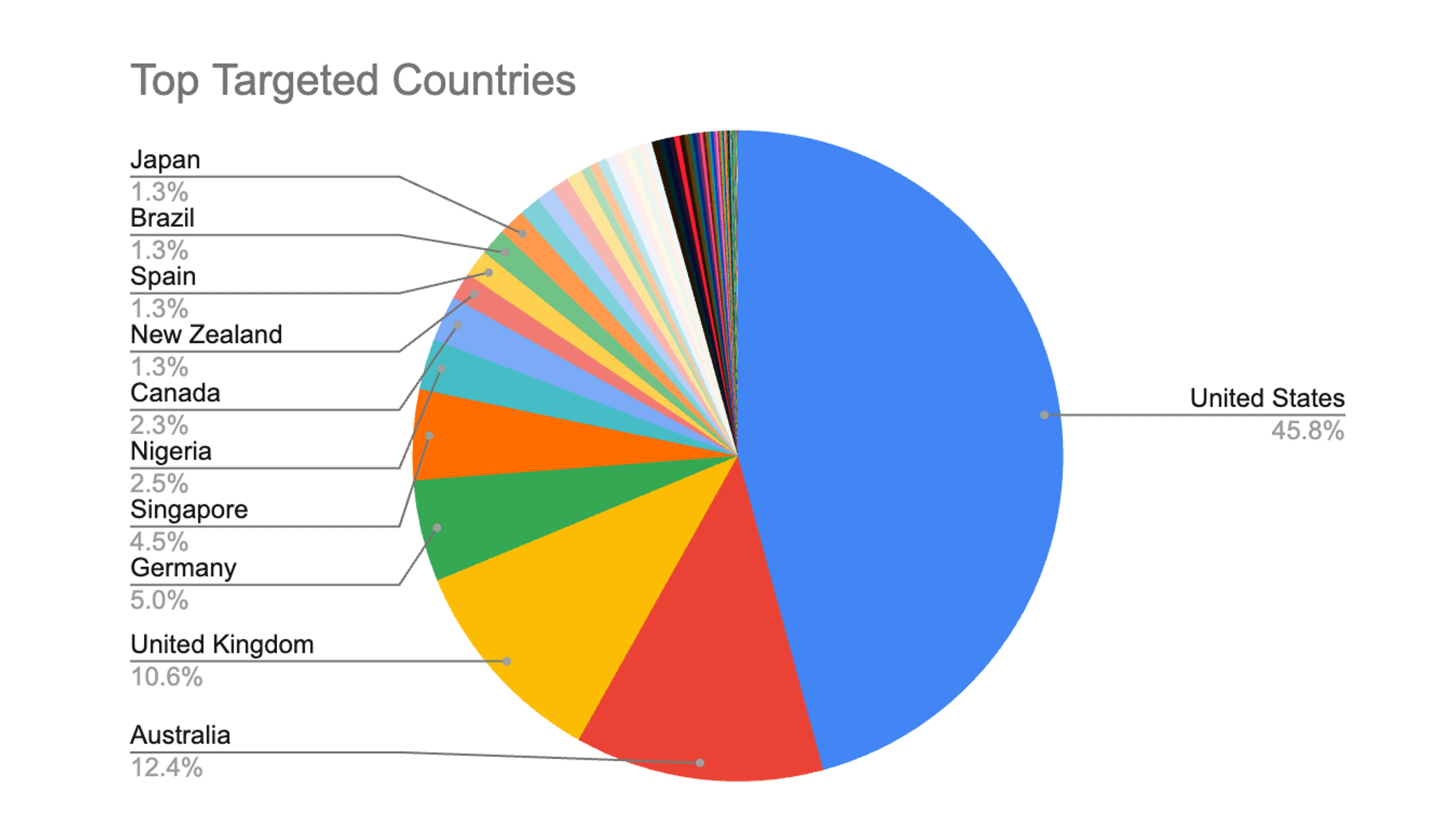
The US, in particular, drew nearly half of all observed attacks, consistent with its dominant share of global Black Friday spending. Australia and the UK followed, reflecting strong regional participation in holiday sales events and an attacker strategy aimed at exploiting high-demand markets where automated activity can more easily blend in with legitimate traffic.
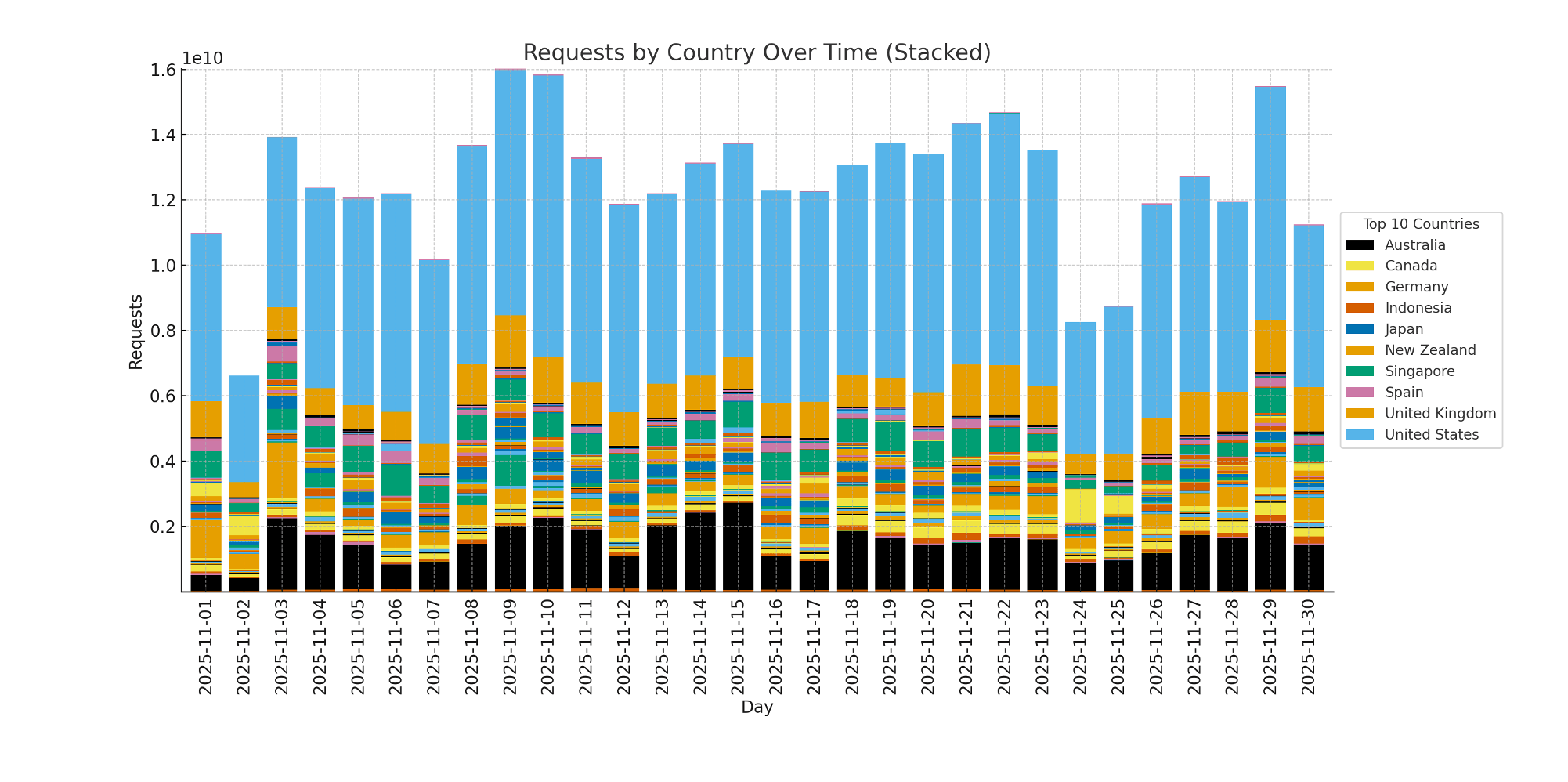
For retailers operating in these geographies, the data underscores the importance of region-aware threat monitoring and the need to maintain heightened vigilance throughout the extended holiday weekend.
Attack Patterns Reveal Automation, ATO Prep, and Abuse at Scale
Based on attacker activity observed over the holiday shopping weekend, several clear patterns emerged, showing a mix of high-volume automation, credential-based attacks, and spam and proxy abuse. Overall, the attack data suggests that adversaries were focused on the following behaviors:
1. Heavy Use of Known Bad Bots and Automated Browsers
A significant portion of malicious traffic came from known automated frameworks, including headless browsers and scripted tools designed to mimic real users. This type of activity typically supports:
- Large-scale login attempts
- Price, inventory, or content scraping
- Testing of checkout, promotion, and product pages for weaknesses
Attackers were industrializing their activity using automation that can rapidly adapt during peak events.
2. Preparing and Executing Account Takeover (ATO)
We observed high levels of activity associated with login reconnaissance and credential-testing behavior, indicating attempts to stage or execute ATO. Attackers were:
- Testing large volumes of username/password combinations
- Probing login endpoints to identify which attempts were blocked, challenged, or allowed
- Taking advantage of elevated holiday traffic to blend their activity into normal user patterns
This aligns with typical seasonal fraud behavior, where attackers target stored payment methods, loyalty balances, and customer identities.
3. Evading Detection Through Proxies and Client Impersonation
A large volume of traffic originated from anonymous proxies, VPNs, and other anonymization services, combined with indicators of client spoofing meant to disguise automation. Attackers were:
- Rapidly rotating IP addresses
- Using advanced bots, attempting to masquerade as legitimate browsers
- Using more simple bots, which use fingerprints or user agents that fell outside normal human patterns
In response, much of this traffic triggered JavaScript challenges or CAPTCHA enforcement, forcing suspicious clients to prove they were human.
4. Abusing Forms and Content Channels for Spam
We also observed activity consistent with comment spam, referrer manipulation, and other low-effort abuse aimed at exploiting retail sites as platforms for unwanted advertising or redirection. This typically includes:
- Submitting spam content through comment or feedback forms
- Inserting malicious or low-quality URLs via referrer fields
- Attempting to poison analytics or direct traffic elsewhere
While not as immediately damaging as ATO, these campaigns can harm site performance, customer trust, and brand analytics.
What This Means for Retailers
Black Friday 2025 reinforced several themes:
- The peak holiday season is widening.
High traffic persisted later into the weekend than in prior years. Retailers should consider extending peak staffing and monitoring coverage accordingly. - Attackers are increasingly using shopper traffic as camouflage.
Surges in human activity closely mirror surges in automated abuse. Retailers need strong bot detection, fingerprinting, and behavioral analysis—not just rate limiting. - API security is now as important as web application security.
Many of the top targeted URLs were APIs tied to data, personalization, or analytics. These endpoints often sit behind the UI and may not receive the same scrutiny as consumer-facing pages. - Geographic targeting is aligned with opportunity.
The US, Australia, and UK remain prime markets for both legitimate and malicious traffic. Retailers serving these regions must expect elevated attack pressure during every promotional period.
Conclusion
This year’s Black Friday illustrated both consumer resilience and the evolving sophistication of attackers. Retailers saw new sales records, and attackers took advantage of the same moment to blend in, scale operations, and probe for weaknesses.
As the holiday season continues, retailers should ensure that defenses are calibrated for:
- Sustained high traffic (not just one peak day)
- Increased bot sophistication
- ATO protection
- Region-specific targeting aligned with revenue hotspots
By understanding the patterns we saw during Black Friday, retailers can prepare for the continued wave of holiday traffic and ensure a safer, smoother experience for their customers through the end of the year.
The post Black Friday 2025 in Review: What Retailers Need to Know About This Year’s Holiday Shopping Season appeared first on Blog.