November 2025 saw a significant 69% decrease in high-impact vulnerabilities, with Recorded Future’s Insikt Group® identifying 10 vulnerabilities requiring immediate attention, down from 32 in October.
What security teams need to know:
- Fortinet leads concerns: Two critical FortiWeb vulnerabilities (CVE-2025-64446 and CVE-2025-58034) are under active exploitation
- LANDFALL spyware campaign: Threat actors weaponized Samsung’s image processing flaw (CVE-2025-21042) for zero-click Android attacks
- Public exploits proliferate: Seven of ten vulnerabilities have public proof-of-concept code available
- OS Command Injection and Out-of-bounds Write were tied as the most common weakness types
Bottom line: The reduced volume shouldn’t signal reduced vigilance. November’s vulnerabilities demonstrate that threat actors favored quality over quantity in their exploitation campaigns.
Quick Reference: November 2025 Vulnerability Table
All 10 vulnerabilities below were actively exploited in November 2025.
Score
Table 1: List of vulnerabilities that were actively exploited in November based on Recorded Future data (Source: Recorded Future)
Key Trends: November 2025
Vendors Most Affected
- Fortinet dominated with two critical FortiWeb vulnerabilities, both enabling remote exploitation
- Microsoft faced a kernel-level race condition affecting all modern Windows versions
- Samsung saw the weaponization of an image processing vulnerability for sophisticated mobile attacks
- Additional affected vendors: Gladinet, Google, Oracle, WatchGuard, CentOS, and Autonomy (OpenPLC)
Most Common Weakness Types
- CWE-78 – OS Command Injection (tied for first)
- CWE-787 – Out-of-bounds Write (tied for first)
- CWE-284 – Improper Access Control
- CWE-362 – Race Condition
- CWE-306 – Missing Authentication for Critical Function
Threat Actor Activity
LANDFALL Android spyware campaign marked November’s most sophisticated operation:
- Exploited CVE-2025-21042 for zero-click remote code execution on Samsung devices
- Targeted Middle Eastern countries (Iraq, Iran, Turkey, Morocco) with commercial-grade spyware
- Deployed via weaponized DNG image files through WhatsApp
- Achieved persistent device compromise without user interaction
- Demonstrated advanced anti-analysis and SELinux bypass capabilities
Priority Alert: Active Exploitation
These vulnerabilities demand immediate attention due to confirmed exploitation in the wild.
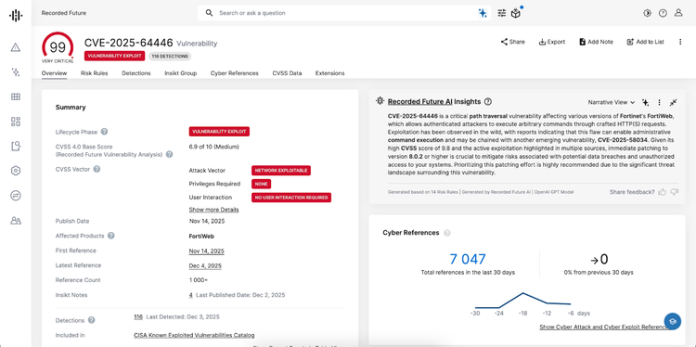
CVE-2025-64446 | Fortinet FortiWeb
Risk Score: 99 (Very Critical) | CISA KEV: Added November 14, 2025
Why this matters: Unauthenticated attackers can bypass authentication entirely and create administrative accounts. With 4,768 exposed FortiWeb instances globally, this represents a critical internet-facing risk.
Affected versions: FortiWeb 8.0.0-8.0.1, 7.6.0-7.6.4, 7.4.0-7.4.9, 7.2.0-7.2.11, 7.0.0-7.0.11
Immediate actions:
- Apply Fortinet’s security updates (8.0.2, 7.6.5, 7.4.10, 7.2.12, or 7.0.12)
- Monitor for POST requests to
/api/v2.0/cmd/system/admin%3F/../../../cgi-bin/fwbcgi - Check for unauthorized admin accounts created since October 2025
- Review logs for Base64-encoded CGIINFO headers
- Disable HTTP/HTTPS on internet-facing interfaces if patching is delayed
Exposure: ~4,768 FortiWeb instances visible on Shodan (Netherlands, US, Germany, Italy, Peru)