Actively exploited as a zero-day in data theft and extortion campaigns, with activity linked to the Cl0p ransomware group. Successful exploitation enables complete takeover of Oracle Concurrent Processing, opening the door to lateral movement, sensitive data exfiltration, and potential ransomware deployment. – Read more
Latest article
Leveraging OSINT Tools for Enhanced Cybersecurity Threat Intelligence
Open Source Intelligence (OSINT) has become a cornerstone of cybersecurity threat intelligence. In today’s digital landscape, organizations face a constant barrage of cyber threats,...
BreachForums (2025) – 324,449 breached accounts
In October 2025, a reincarnation of the hacking forum BreachForums, which had previously been shut down multiple times, was taken offline by a coalition...
Trend Micro patches critical flaws in its Apex Central software
Security company Trend Micro has been compelled to issue a patch for its own Apex Central software management tool after...
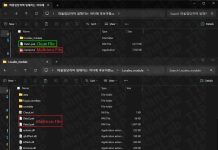
Metasploit Wrap-Up 01/09/2026
RISC-V PayloadsThis week brings more RISC-V payloads from community member bcoles. One provides a new adapter which allows RISC-V payloads to be converted to commands...