|
What is the Attack? |
On November 24, 2025, Shai Hulud launches a second supply-chain attack, compromising Zapier, ENS, AsyncAPI, PostHog, and Postman, along with over 25,000 affected repositories across ~350 unique users. On September 8, 2025, attackers phished the npm maintainer “qix” and stole their two-factor authentication (2FA) credentials. With that access, they published malicious versions of some very popular npm packages (including debug, chalk, and ansi-styles). The impact is considered high risk for applications that serve frontend JavaScript, especially those handling payments, cryptocurrency, or wallet flows. Reports indicate that these compromised versions were live for about two hours before removal. According to the CISA Alert on this incident, the campaign also involved a self-replicating worm publicly known as “Shai-Hulud,” which compromised over 500 packages. After gaining initial access, the malicious actor deployed malware that scanned environments for sensitive credentials. The attacker specifically targeted GitHub Personal Access Tokens (PATs) and API keys for major cloud platforms, including Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. |
|
What is the recommended Mitigation? |
|
|
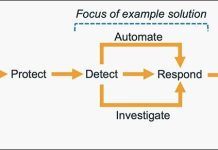
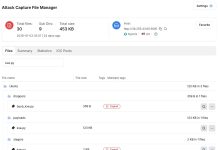
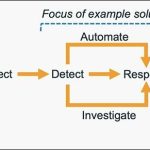
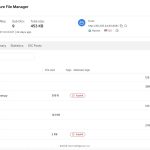
What FortiGuard Coverage is available? |
|
Welcome!Log into your account