Learn more about the Shai-Hulud 2.0 npm worm. – Read more
Latest article
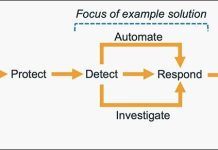
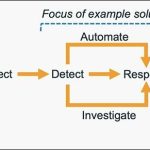
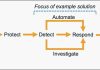
How to get started with security response automation on AWS
At AWS, we encourage you to use automation. Not just to deploy your workloads and configure services, but to also help you quickly detect...
I’m locked in!
Welcome to this week’s edition of the Threat Source newsletter.I’ve struggled a lot over the last few years with balance. I want to follow the...
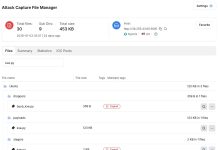
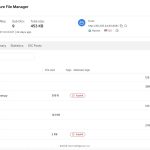
Exposed Open Directory Leaks BYOB Framework Across Windows, Linux, and macOS
Threat researchers have uncovered an actively serving command and control server hosting a complete deployment of the BYOB framework following the discovery of an...
Identitäten im Fokus von Cyberkriminellen
Cyberkriminelle haben es inzwischen vermehrt auf digitale Identitäten abgesehen.khunkornStudio – shutterstock.com Der State of Incident Response Report 2026 von Eye...