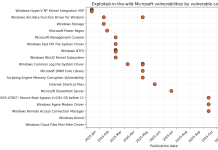
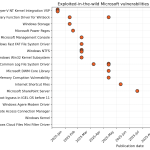
A critical deserialization vulnerability in GoAnywhere MFT’s License Servlet (CVSS 10.0) is actively being exploited in the wild. The flaw allows attackers with a forged license response signature to deserialize arbitrary objects, which can lead to command injection and remote code execution (RCE). FortiGuard telemetry shows sustained, high-volume exploitation attempts against GoAnywhere MFT instances. – Read more
Latest article
Critical bug in popular vm2 Node.js sandboxing library puts projects at risk
A critical vulnerability has been patched in vm2, a widely used library for the Node.js JavaScript runtime that allows untrusted...
$95M Payout: Apple Begins Compensating Users in Siri Eavesdropping Case
Apple has started issuing Siri privacy settlement payouts, with claimants seeing deposits as low as $8 per device from a $95 million fund.
The post...
Burner phones and lead-lined bags: a history of UK security tactics in China
Starmer’s team is wary of spies but such fears are not new – with Theresa May once warned to get dressed under a duvetWhen...
Patch Tuesday and the Enduring Challenge of Windows’ Backwards Compatibility
IntroductionIf you received an email with the subject “I LOVE YOU” and an attachment called “LOVE-LETTER-FOR-YOU.TXT”, would you open it? Probably not, but back...