Google Cloud Platform (GCP) Google Security Operations SIEM Tenant Service Account of the SecOps Instance Access Token Leak
Tenable Research has identified and responsibly disclosed a safety mechanism bypass vulnerability in Google Security Operations. This flaw allowed an attacker to leak the access token of the highly privileged SIEM tenant service account, leading to a significant privilege escalation.
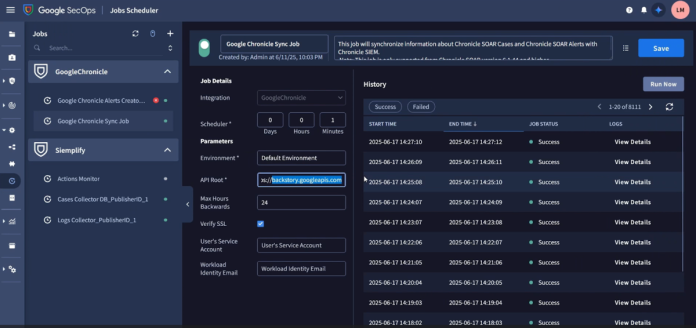
This vulnerability was rooted in the handling of API connections within Google Security Operations’ job scheduler. When a scheduled job was configured with a custom integration, an attacker could manipulate the API root parameter to point to an external, attacker-controlled server.
By altering this parameter, the attacker could force the system to use a different code path than the default. This change in execution flow caused the job to use a more permissive set of credentials—specifically, the access token of the SIEM tenant service account. This service account, which has the cloud-platform scope, possesses extensive permissions across the entire Google Cloud project. By capturing this token on their external server, an attacker could assume the identity of the service account and perform a wide range of unauthorized actions, including accessing, exfiltrating, or modifying data in the SIEM.
Proof of Concept
- Access Google Security Operations → Response → Jobs Scheduler
- Choose the “Google Chronicle Alerts Creator Job”
- Input your external server in the API ROOT parameter
- Optional: Untick “Verify SSL” if necessary
- Run the job by pressing the play button
- The access token should be in an HTTP request that was sent to your external server