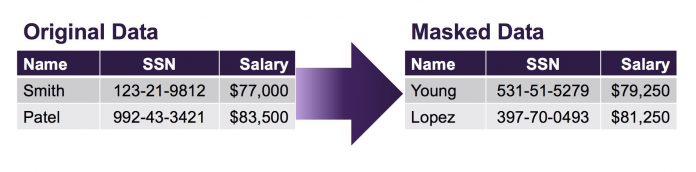
Three Reasons Why GDPR Encourages Pseudonymization
The General Data Protection Regulation (GDPR) is the European Union’s new data regulation designed to provide individuals with rights and protections over their personal data that is collected or created by businesses or government entities. It unifies data protection regulation across all member states of the European Union (EU) and is set to replace the Data Protection Directive. The...
Centrify Joins FIDO Alliance and Expands Partnership with Yubico
Centrify has been busy building innovative technology and powerful partnerships. This post will talk about a longtime partnership, cool tech, and a deeper level of integration. Centrify and Yubico have been partners for more than three years already and work together with joint customers, in the field, and at a corporate level.
Centrify and Yubico U2F Integration
To further its move...
The Year in Review: Centrify Builds Momentum
The Centrify solution made great strides in 2017, chronicled in Part I of this blog. Product enhancements, combined with the market’s growing understanding of the essential role identity plays in effective cybersecurity propelled the business forward. Here are some additional business highlights:
The Centrify/Ponemon study
Early in 2017, Centrify sponsored a Ponemon research study
to discover the business and financial impact of...
Happy IR in the New Year!
At the end of last year Mr. Jake Williams from aka @MalwareJake asked a very important question about Lack of visibility during detecting APT intrusions in twitter. Results show us that endpoint analysis is the most important part of any research connected with APTs. Also, for sure endpoint forensics is critical during any Incident Response (IR) because in many...
Women in Tech and Career Spotlight: Jerusalem Bicha
We conclude our series featuring women in tech at Imperva with an interview with Jerusalem Bicha, network operations team lead at Imperva. We talked about her path to a career in cybersecurity.
Tell us how you got into cybersecurity.
JB: I actually don’t have a degree. My career in cybersecurity happened by accident when I served in the Israeli Army. I...
The Year in Review: Rethink Security
During a year of high-profile breaches like Equifax, HBO and Uber, as well as the realization that Yahoo’s highly-publicized 2013 breach compromised the accounts of all three billion of its users, the tide started to turn in 2017. Organizations, industry experts, thought leaders, the media and even consumers began to understand the status quo simply isn’t working. Ideas like...
Nhash: petty pranks with big finances
According to our data, cryptocurrency miners are rapidly gaining in popularity. In an earlier publication we noted that cybercriminals were making use of social engineering to install this sort of software on users’ computers. This time, we’d like to dwell more on how exactly the computers of gullible users start working for cybercriminals.
Beware freebies
We detected a number of similar...
Travle aka PYLOT backdoor hits Russian-speaking targets
.travle-big-table td{border:1px solid #eee!important}.travle-big-table td{padding: 10px;}
At the end of September, Palo Alto released a report on Unit42 activity where they – among other things – talked about PYLOT malware. We have been detecting attacks that have employed the use of this backdoor since at least 2015 and refer to it as Travle. Coincidentally, KL was recently involved in an...
Jack of all trades
Nowadays, it’s all too easy to end up with malicious apps on your smartphone, even if you’re using the official Google Play app store. The situation gets even worse when you go somewhere other than the official store – fake applications, limited security checks, and so on. However, the spread of malware targeting Android OS is not limited to...
Kaspersky Security Bulletin. Overall statistics for 2017
All the statistics used in this report were obtained using Kaspersky Security Network (KSN), a distributed antivirus network that works with various anti-malware protection components. The data was collected from KSN users who agreed to provide it. Millions of Kaspersky Lab product users from 213 countries and territories worldwide participate in this global exchange of information about malicious activity.
The year...