Financial threats in H1 2019
Introduction and methodology
Financial cyberthreats are malicious programs that attack users of online banking services, electronic money, cryptocurrency and other similar services, as well as threats aimed at gaining access to financial organizations and their infrastructure. Kaspersky experts regularly analyze the statistics that the company’s products anonymously send to the cloud infrastructure of the Kaspersky Security Network (KSN) in case...
Industrial Cybersecurity from Tripwire Enterprise
Industrial Cybersecurity from Tripwire Enterprise #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff;...
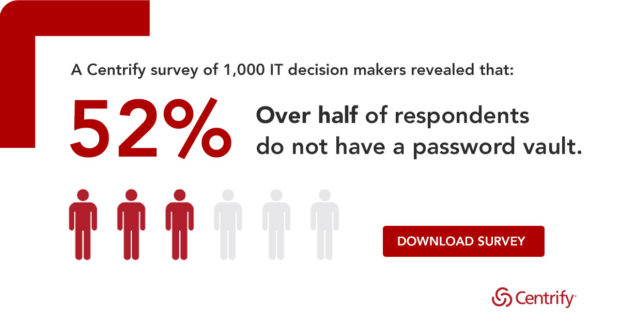
52% of Companies Don’t have a Password Vault for Privileged Access – Here’s Your Chance!
Over the first half of 2019, Centrify issued two research reports about the adoption of Privileged Access Management (PAM) solutions and the maturity of organizations on the path to Zero Trust Privilege.
The first report, “Privileged Access Management in the Modern Threatscape” published in February 2019, surveyed 1,000 IT decision makers in the U.S. and U.K. The main takeaway from...
Enabling Faster DDoS Mitigation for Cloud Assets
The cloud journey was considered a visionary approach less than a decade ago. Today, more than half of organizations rely on a cloud provider, and are planning to expand their portfolios across multiple cloud platforms, as part of their ongoing digital transformation.
Is the so-called cloud promise a reality today? To some extent, yes. However, it’s also critical for any...
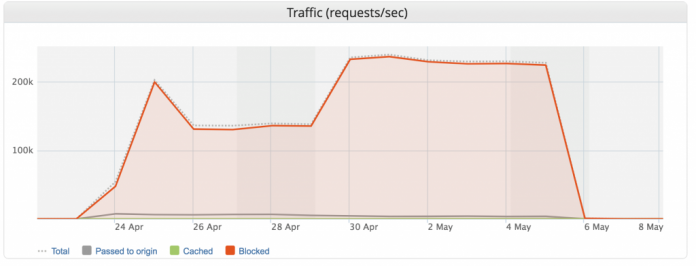
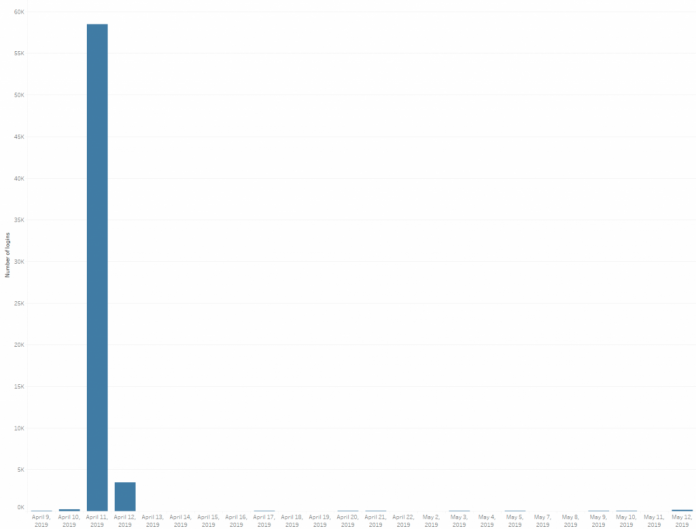
Imperva Blocks Our Largest DDoS L7/Brute Force Attack Ever (Peaking at 292,000 RPS)
Imagine you’re a developer building a new web application. You’ve followed all of the security best practices, hired a reputable penetration testing company before launch, and gone through extensive bug fixing to remove any vulnerabilities. However, would you be confident that your application could survive the largest and longest DDoS attack that you’d ever seen?
Targeting the authentication component of...
New 3-Second DDoS Mitigation SLA is 3x Faster and the Industry’s Best
Back in 2018, we made waves with a groundbreaking DDoS Mitigation SLA (service level agreement) for our DDoS Protection service that guaranteed to mitigate DDoS attacks in under 10 seconds. Now, we’ve upped the ante to ensure DDoS attack mitigation with a new, industry-best three seconds-or-less guarantee.
The Importance of Time to Mitigation (TTM)
This commitment sets a new standard for...
Medical Device Cybersecurity
Medical Device Cybersecurity #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff; } h1,.h1{...
How to steal a million (of your data)
Any user data — from passwords for entertainment services to electronic copies of documents — is highly prized by intruders. The reason is simply that almost any information can be monetized. For instance, stolen data can be used to transfer funds to cybercriminal accounts, order goods or services, and, if the desire or opportunity is lacking to do it...
How Account Takeover Botnets Outsmart Traditional Security Controls
Account Takeover (ATO) describes when an online account is accessed and/ or used by someone other than its legitimate owner, usually for malicious purposes. Account Takeover attacks happen when an attacker is trying to get unauthorized access to an account or when the account has already been compromised and the attacker uses the account for a malicious purpose, such...