Gartner Security & Risk Management Summit 2018
Gartner Security & Risk Management Summit 2018
June 4th – 7th | National Harbor, MD
- Read more
SynAck targeted ransomware uses the Doppelgänging technique
The Process Doppelgänging technique was first presented in December 2017 at the BlackHat conference. Since the presentation several threat actors have started using this sophisticated technique in an attempt to bypass modern security solutions.
In April 2018, we spotted the first ransomware employing this bypass technique – SynAck ransomware. It should be noted that SynAck is not new – it...
World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my life, if Outlook or Android doesn’t serve me a popup reminder, I’m oblivious to it.
But this one commanded my attention, not only because of the never-ending news coverage we see about high-profile breaches, but also...
Who’s who in the Zoo
ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation infect Android devices using several generations of malware, with the attackers including new features in each iteration. We label them from v1-v4, with v4 being the most recent version deployed in 2017. From the technical...
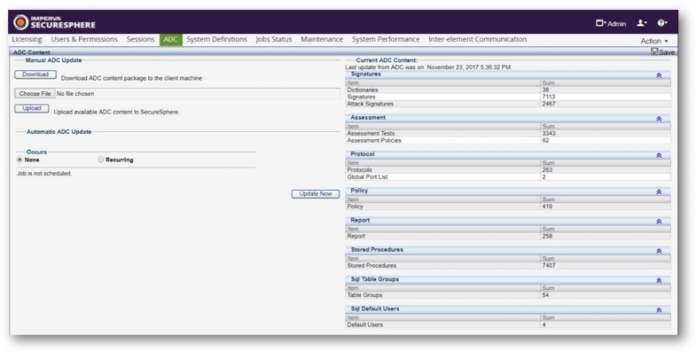
Configuring Imperva SecureSphere for GDPR Compliance: Part One
Time is running out. 23 days until GDPR enforcement
The GDPR effective date is less than a month away and, given the significant risk and potential costs associated with a failure to comply, organizational readiness efforts continue to mount. GDPR non-compliance penalties can be severe (up to 79 times higher than existing guidelines), and GDPR applies to any organization of...
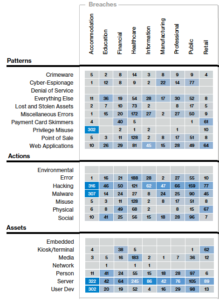
Insights from the Verizon 2018 Data Breach Investigation Report
The 2018 Verizon Data Breach Investigation Report (DBIR) was published in early April, reporting on 53,308 security incidents and 2,216 data breaches from 67 contributors in 65 countries.
It’s an important read for organizational leaders, and cyber professionals to find data-driven evidence of industry-specific incident patterns. It’s also important to distinguish incidents from breaches. A breach is an incident that...
Securing the Entire Container Stack, Lifecycle and Pipeline
Securing the Entire Container Stack, Lifecycle and Pipeline #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
DevSecOps Gathers More of the Spotlight at RSA 2018
Nearly 1,200 security professionals recently attended the DevOps Connect: DevSecOps Day at the 2018 RSA Conference at San Francisco’s Moscone Center.
Now in its fourth year, DevSecOps Day featured presentations and panel discussions on the role of security in the world of DevOps. DevOps thought leaders, security experts, and vendors shared success stories, insights, and challenges they faced in their...
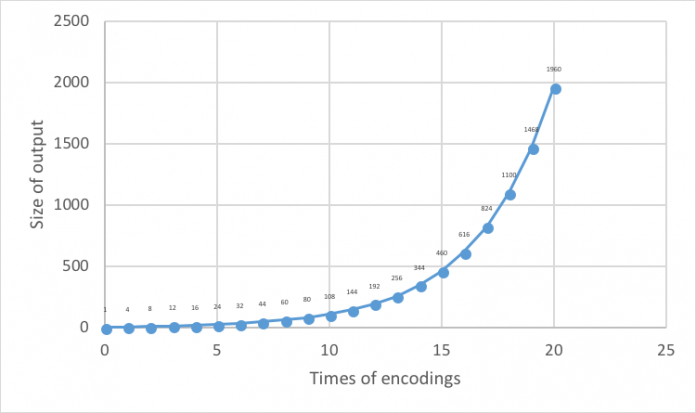
The Catch 22 of Base64: Attacker Dilemma from a Defender Point of View
Web application threats come in different shapes and sizes. These threats mostly stem from web application vulnerabilities, published daily by the vendors themselves or by third-party researchers, followed by vigilant attackers exploiting them.
To cover their tracks and increase their attack success rate, hackers often obfuscate attacks using different techniques. Obfuscation of web application attacks can be extremely complicated, involving...