Electronic Health Record Systems Under Attack
Electronic Health Record Systems Under Attack #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
Centrify and SailPoint Join Forces to Apply Zero Trust Security Best Practices to Identity Governance
Today, Centrify is proud to announce the integration of the Centrify Privileged Access Service with SailPoint® Technologies IdentityIQ solution.
This integration provides joint customers with a single pane of glass for a privileged user’s entitlements and enables issuing access requests for accounts, systems, and existing roles that are controlled by the Centrify Privileged Access Service. This allows for centralized management...
IT threat evolution Q1 2018. Statistics
Q1 figures
According to KSN:
Kaspersky Lab solutions blocked 796,806,112 attacks launched from online resources located in 194 countries across the globe.
282,807,433 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 204,448 users.
Ransomware attacks were registered on the computers of...
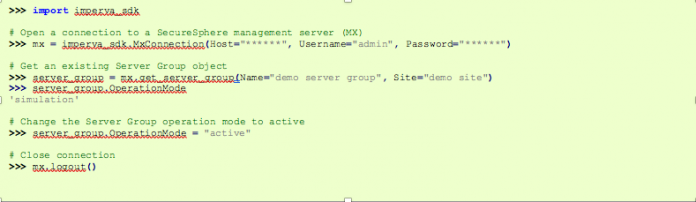
Imperva Python SDK – We’re All Consenting SecOps Here
Managing your WAF can be a complicated task. Custom policies, signatures, application profiles, gateway plugins… there’s a good reason ours is considered the best in the world.
Back when security teams were in charge of just a handful of WAF stacks and a few dozen applications, things were relatively manageable. Today, however, with the shift to cloud and microservices, organizations...
OPC UA security analysis
This paper discusses our project that involved searching for vulnerabilities in implementations of the OPC UA protocol. In publishing this material, we hope to draw the attention of vendors that develop software for industrial automation systems and the industrial internet of things to problems associated with using such widely available technologies, which turned out to be quite common. We...
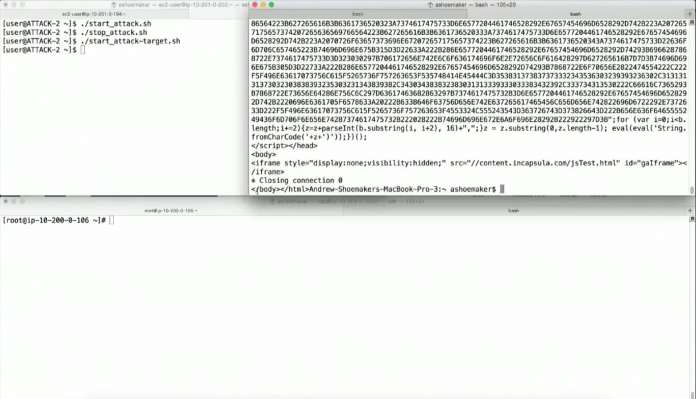
Want to See What A Live DDoS Attack Looks Like?
We’re fortunate enough to have had Andy Shoemaker, founder of NimbusDDoS, and our own Ofer Gayer chat about DDoS attacks and shed some light on the gaps in many people’s understanding of the threats out there.
In a new BrightTALK webinar alongside Imperva Senior Product Manager, Ofer, Andy discusses the trade-offs of manual versus automatic mitigation strategies, and to that effect showed...
Jumpstarting Your Cyberdefense Machine with CIS Controls V7
Jumpstarting Your Cyberdefense Machine with CIS Controls V7 #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
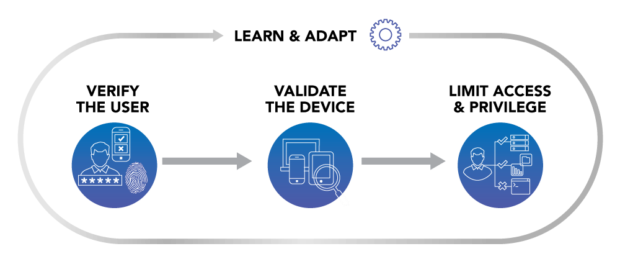
How to Operationalize the Zero Trust Security Pillar ‘Limit Access & Privilege’ with ServiceNow
An easy way for a cyber-attacker to gain access to sensitive data is by compromising an end user’s identity and credentials. Things get even worse if a stolen identity belongs to a privileged user, who has even broader access, and therefore provides the intruder with “the keys to the kingdom.”
As a result, it’s not surprising that, according to Forrester,...

![[VitalQIP Migration Series] Part 1: Three Reasons Why VitalQIP Migration Should Be on Your Radar](http://www.dataproof.co.za/wp-content/uploads/2018/05/vitalqip-migration-series-part-1-three-reasons-why-vitalqip-migration-should-be-on-your-radar.jpg)