FIFA public Wi-Fi guide: which host cities have the most secure networks?
We all know how easy it is for users to connect to open Wi-Fi networks in public places. Well, it is equally straightforward for criminals to position themselves near poorly protected access points – where they can intercept network traffic and compromise user data.
A lack of essential traffic encryption for Wi-Fi networks where official and global activities are taking...
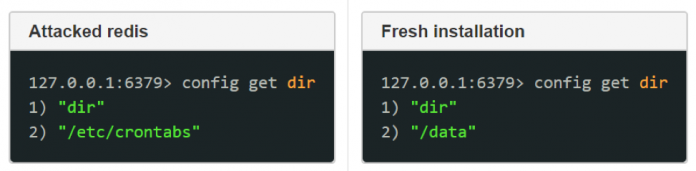
New research shows 75% of ‘open’ Redis servers infected
Since our initial report on the RedisWannaMine attack that propagates through open Redis and Windows servers, we’ve been hearing about more and more attacks on Redis servers.
Redis is a great tool, it can serve as in-memory distributed database, cache or a message broker and is widely popular. Redis is aimed at high performance and in doing so, some other...
Netkids
Children today are completely at home in the digital space. They use digital diaries and textbooks at school, communicate via instant messaging, play games on mobile devices (not to mention PCs and consoles), and create mini masterpieces on tablets and laptops. This total immersion in the digital universe is a concern for many parents, but if they want their...
What’s in it for Consumers? The Top 5 Privacy Benefits of the GDPR
The General Data Protection Regulation, or GDPR for short, is a major new European privacy law that went into effect on May 25. GDPR will radically reframe our relationship with the organisations that store and process our data. From Amazon to the UK National Health Service (NHS), organisations around the world are desperately racing to ensure compliance, even after...
MITRE ATT&CK Matrix with CIS Controls and Tripwire mapping
MITRE ATT&CK Matrix with CIS Controls and Tripwire mapping #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100%...
Five Ways Imperva Attack Analytics Helps You Cut Through the Event Noise
The maddening volume of events security teams have to deal with each day is growing at an exponential pace, making it increasingly difficult to effectively analyze and process credible threats. As more organizations move to cloud-based solutions, applications now reside at multiple locations – on premises, in the cloud or in a hybrid environment – compounding the problem of investigating...
Trojan watch
We continue to research how proliferation of IoT devices affects the daily lives of users and their information security. In our previous study, we touched upon ways of intercepting authentication data using single-board microcomputers. This time, we turned out attention to wearable devices: smartwatches and fitness trackers. Or more precisely, the accelerometers and gyroscopes inside them.
From the hoo-ha surrounding...
See If You’re GDPR-Ready With Our Last-Minute Checklist
Time’s just about run out to get all your ducks in a row for the EU’s General Data Protection Regulation (GDPR) going into effect on May 25, and we’ve put together a little refresher toolkit to help you dot your Is and cross your Ts.
Whether you’re planning on sticking to the new GDPR guidelines or consider yourself safe, the...
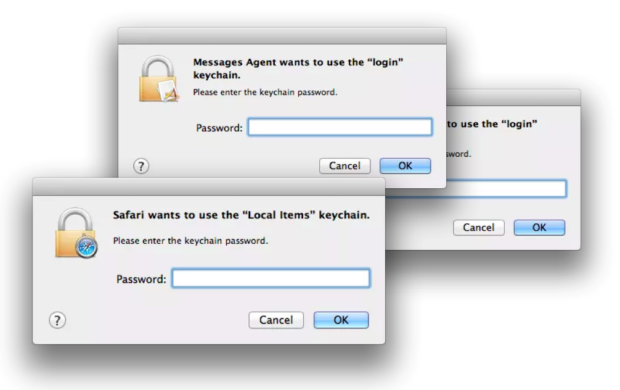
Sync Your Jaws Into Mac Keychain
“Well this is not a boat accident! It wasn’t any propeller! It wasn’t any coral reef! And it wasn’t Jack the Ripper! It was Keychain.”
Just uttering the dreaded word Keychain can cause a Mac user or Admin to break out in a cold sweat. We’ve all seen the pop ups.
<Cue the ominous music>
Apple first introduced the Keychain in Mac...