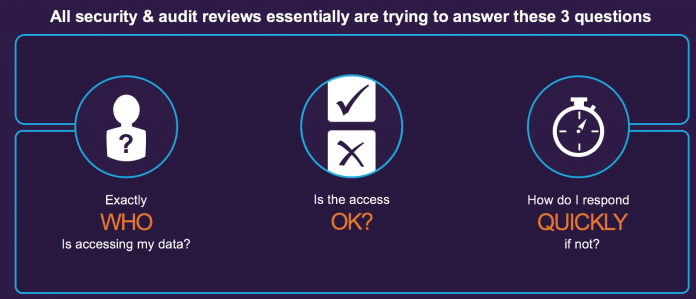
Multi-Cloud Security Best Practice Guide
Multi-Cloud Security Best Practice Guide #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff;...
A Quick-Start Introduction to Database Security: An Operational Approach
The recent SingHealth data breach incident exposed around 1.5 million patients’ records. In its aftermath, the Cyber Security Agency of Singapore published a set of security measures aimed at improving the protection of Personally Identifiable Information (PII) data.
The recommended security measures covered several facets of IT security domains:
Data governance and data management lifecycle
Identity access management around user rights review
Tightened...
Imperva to Acquire DevOps Security Leader Prevoty
Today, we announced that we entered into an agreement to acquire Prevoty, an innovator and leader in building application security that can block attacks and monitor interactions inside application stacks using DevOps and agile development. I’m incredibly excited that the Prevoty team will join Imperva.
Our vision is to lead the world’s fight to keep applications and data safe from...
Fortnite Scammers Approaching $1m in Annual Takings
When something seems too good to be true, it probably is. It’s a hard lesson to learn and, in this case, one that’s being taught by scammers. The perpetrators are abusing the fact that online players of Battle Royale games may be very eager to get free in-game currency and items, and are willing to go to pretty risky...
A mining multitool
Recently, an interesting miner implementation appeared on Kaspersky Lab’s radar. The malware, which we dubbed PowerGhost, is capable of stealthily establishing itself in a system and spreading across large corporate networks infecting both workstations and servers. This type of hidden consolidation is typical of miners: the more machines that get infected and the longer they remain that way, the...
Gartner and Centrify Agree – PAM is #1 Security Project for 2018
CISOs are overwhelmed with a multitude of projects that are pulling at their time and resources. All of these projects feel important and usually will have some benefit, but nobody has the time or budget to do it all.
So which projects will give you the biggest bang for your buck? How do security professionals prioritize these initiatives?
At this year’s...
A study of car sharing apps
The growing popularity of car sharing services has led some experts to predict an end to private car ownership in big cities. The statistics appear to back up this claim: for example, in 2017 Moscow saw the car sharing fleet, the number of active users and the number of trips they made almost double. This is great news, but...
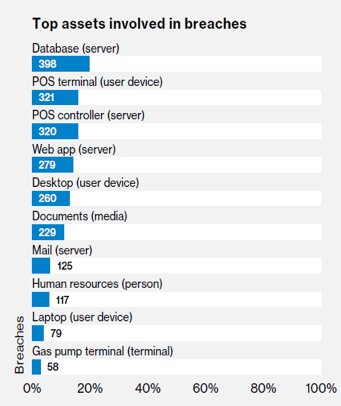
The Data Breach ‘Kill Chain’: Early Detection is Key
Today, organizations rely heavily on data, with a big portion of that data made up of sensitive information. As organizations become the custodians of more and more sensitive information, the frequency of data breaches increases accordingly. In some cases, the origin of a data breach is outside of the organization, with hackers succeeding in evading organizations by compromising accounts;...
Threat Actors in Critical Infrastructure: New Trends and Risk Factors
Threat Actors in Critical Infrastructure: New Trends and Risk Factors #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0;...