Dark Tequila Añejo
Dark Tequila is a complex malicious campaign targeting Mexican users, with the primary purpose of stealing financial information, as well as login credentials to popular websites that range from code versioning repositories to public file storage accounts and domain registrars.
A multi-stage payload is delivered to the victim only when certain conditions are met; avoiding infection when security suites are...
Centrify Interns Reflect on a Summer of Zero Trust
Every summer, Centrify gets an infusion of fresh perspectives and eager learners via our Summer Intern program.
This summer, we had 22 interns join us on our mission to secure enterprise Identity and Access Management with Zero Trust Security. Some have already returned to school, while others are extending their internships due to late school start dates or because they’ve...
Security assessment of corporate information systems in 2017
Each year, Kaspersky Lab’s Security Services department carries out dozens of cybersecurity assessment projects for companies worldwide. In this publication, we present a general summary and statistics for the cybersecurity assessments we have conducted of corporate information systems throughout 2017.
We have analyzed several dozen projects for companies from various sectors, including government bodies, financial organizations, telecommunications and IT companies,...
A Bug in Chrome Gives Bad Actors License to Play ‘20 Questions’ with Your Private Data
In a 2013 interview with The Telegraph, Eric Schmidt, then CEO of Google was quoted as saying: “You have to fight for your privacy or lose it.”
Five years later, with the ‘Cambridge Analytica’ data breach scandal fresh in our memory, Eric Schmidt’s statement rings as a self-evident truth. Similarly clear today is the nature of the “fight”: a grapple for transparency...
Watch: An Account Takeover Attack Using Credential Stuffing, and How to Protect Against It [Video]
As cryptocurrencies continue to grow in diversity, so too do the threats they face, specifically those targeting the cryptocurrency exchange. Now, more than ever, cryptocurrency exchanges are facing security threats in the form of volumetric and application layer DDoS and account takeover (ATO) attacks.
Although the success of cryptocurrency exchanges makes them especially attractive to cybercriminals, attacks of late are taking exchanges by...
Learn the essential DevOps practices that today’s most successful organizations are implementing
Learn the essential DevOps practices that today's most successful organizations are implementing #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important;...
Spam and phishing in Q2 2018
Quarterly highlights
GDPR as a phishing opportunity
In the first quarter, we discussed spam designed to exploit GDPR (General Data Protection Regulation), which came into effect on May 25, 2018. Back then spam traffic was limited to invitations to participate in workshops and other educational events and purchase software or databases. We predicted that fraudulent emails were soon to follow. And...
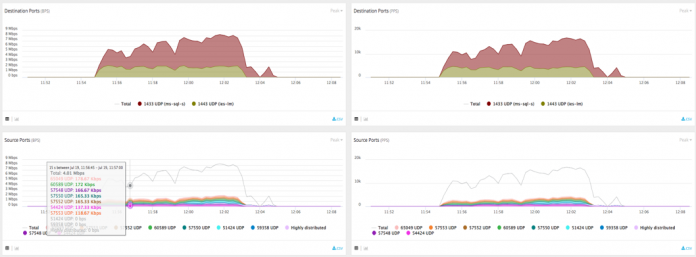
Enhanced Infrastructure DDoS Protection Analytics: Targeted Visibility for Greater Accuracy
We’ve rolled out enhanced infrastructure protection analytics which shows top traffic patterns for traffic flowing through our Incapsula Infrastructure DDoS Protection service.
Imperva clients can now view network statistics categorized by source or destination IPs and ports, or by packet size for protected network ranges. This new addition to our data analytics helps our clients get in-depth visibility into their...