Report: Nearly Half of Security Professionals Think They Could Execute a Successful Insider Attack on Their Organization
As potential threats and entry points into organizations’ databases keep growing, so does the amount of money folks are throwing at detecting and actioning insider threats. In fact, the ballooning amount of money being spent on cybersecurity overall clearly highlights the seriousness with which businesses are tackling the problem in general.
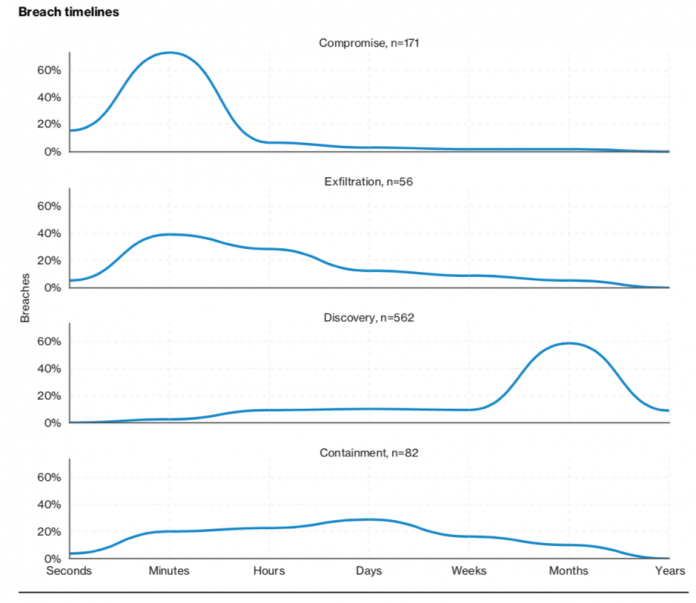
Identifying and containing data breaches
Insider threats are a major...
Loki Bot: On a hunt for corporate passwords
Starting from early July, we have seen malicious spam activity that has targeted corporate mailboxes. The messages discovered so far contain an attachment with an .iso extension that Kaspersky Lab solutions detect as Loki Bot. The malware’s key objective is to steal passwords from browsers, messaging applications, mail and FTP clients, and cryptocurrency wallets. Loki Bot dispatches all its...
Explainer Series: What is Clickjacking?
Here we go, another online trap ready to ensnare unsuspecting – well, until now anyway – users. As if Phishing, Cryptojacking, credential stuffing and old school scamming wasn’t enough, folks really just can’t catch a break these days. Anyway, we’re here to chat about clickjacking, for those of you who aren’t 100% sure what to keep an eye out...
Time For Your Compliance Checkup – How Mercy Health Uses Tripwire to Pass Audits
Time For Your Compliance Checkup – How Mercy Health Uses Tripwire to Pass Audits #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{...
Static vs Dynamic Data Masking: Why Are We Still Comparing the Two?
Earlier this month a leading analyst released their annual report on the state of Data Masking as a component of the overall Data Security sector; which included commentary on what’s known as ‘static’ data masking and an alternative solution known as ‘dynamic’ data masking. And these two solutions have been considered in unison for some time now within the...
Read: Apache Struts Patches ‘Critical Vulnerability’ CVE-2018-11776
On August 22, Apache Struts released a security patch fixing a critical remote code execution vulnerability. This vulnerability has been assigned CVE-2018-11776 (S2-057) and affects Apache Struts versions 2.3 to 2.3.34 and 2.5 to 2.5.16.
The vulnerability was responsibly disclosed by Man Yue Mo from the Semmle Security Research team, check out a detailed description here. An exploit PoC has...
Operation AppleJeus: Lazarus hits cryptocurrency exchange with fake installer and macOS malware
Overview
Lazarus has been a major threat actor in the APT arena for several years. Alongside goals like cyberespionage and cybersabotage, the attacker has been targeting banks and other financial companies around the globe. Over the last few months, Lazarus has successfully compromised several banks and infiltrated a number of global cryptocurrency exchanges and fintech companies.
Kaspersky Lab has been assisting...
Behind the Numbers: Database Authentication and Authorization
Earlier this month, I posted a blog about how most companies I speak with have not implemented a modern database authentication and authorization approach. I also recommended 8 steps IT leaders can take to modernize their database management operations.
Upon reflection, I think an interesting follow up would be to take a look at some numbers that further illustrate the...
Great Cybersecurity with Small Teams
Great Cybersecurity with Small Teams #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff;...