Kaspersky Security Bulletin 2018. Story of the year: miners
Kaspersky Security Bulletin 2018. Statistics
Kaspersky Security Bulletin 2018. Top security stories
Kaspersky Security Bulletin 2018. Threat Predictions for 2019
Cryptocurrency miners that infect the computers of unsuspecting users essentially operate according to the same business model as ransomware programs: the victim’s computing power is harnessed to enrich the cybercriminals. Only in the case of miners, it might be quite a while...
Beginner’s Guide to Tripwire Log Center Industrial Deployments
Beginner's Guide to Tripwire Log Center Industrial Deployments #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
Threat predictions for industrial security in 2019
Kaspersky Security Bulletin: Threat Predictions for 2019
Cryptocurrency threat predictions for 2019
Cyberthreats to financial institutions 2019: overview and predictions
The past few years have been very intense and eventful when it comes to incidents affecting the information security of industrial systems. That includes new vulnerabilities, new threat vectors, accidental infections of industrial systems and detected targeted attacks. In response, last year...
The Rotexy mobile Trojan – banker and ransomware
On the back of a surge in Trojan activity, we decided to carry out an in-depth analysis and track the evolution of some other popular malware families besides Asacub. One of the most interesting and active specimens to date was a mobile Trojan from the Rotexy family. In a three-month period from August to October 2018, it launched over...
Vulnerability Management Buyer’s Guide
Vulnerability Management Buyer's Guide #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff; }...
DirtyCOW Bug Drives Attackers to A Backdoor in Vulnerable Drupal Web Servers
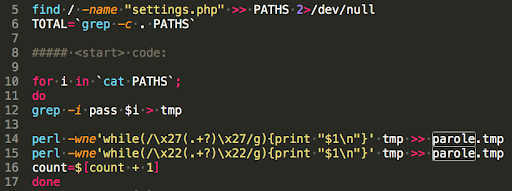
In this post we’ll unpack a short — but no less serious — attack that affected some Linux-based systems, on October 31. Throughout the campaign, the attacker used a chain of vulnerabilities including the infamous Drupalgeddon2 and DirtyCOW, and system misconfigurations to persistently infect vulnerable Drupal web servers and take over user machines.
In the past, remote code execution (RCE)...
With The NASDAQ Bell Ceremony, We Kick Off The Next Leg of Imperva’s Incredible Journey
On Friday morning our CEO Chris Hylen and company execs rung the NASDAQ opening bell in New York, welcoming another day of trading for the world’s second-largest stock exchange; and taking full advantage of the opportunity to celebrate recent corporate milestones for Imperva.
“I’m honored to be standing here today, alongside our management team, representing our amazing employees around the...
Imperva and Amazon Partner to Help Mitigate Risks Associated With Cloud Migration
Helping our customers reduce the risks associated with migrating to the cloud, and preventing availability and security incidents, has been a major development focus for Imperva over the last several years.
Why the partnership matters
Although cloud service providers take a host of IT management burdens off of your shoulders when using their platforms, service level agreements (SLA) for platform...
Black Friday alert
Banking Trojans traditionally target users of online financial services; looking for financial data to steal or building botnets out of hacked devices for future attacks. However, over time, several of these banking Trojans have enhanced their functionality, launching new variants and extending their range. Some are now able to obtain root access to infected devices, perform transactions, inject other...