Threats to users of adult websites in 2018
More graphs and statistics in full PDF version
Introduction
2018 was a year that saw campaigns to decrease online pornographic content and traffic. For example, one of the most adult-content friendly platforms – Tumblr – announced it was banning erotic content (even though almost a quarter of its users consume adult content). In addition, the UK received the title of...
How to introduce security without losing the benefits of containers
How to introduce security without losing the benefits of containers #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0;...
ATM robber WinPot: a slot machine instead of cutlets
Automation of all kinds is there to help people with their routine work, make it faster and simpler. Although ATM fraud is a very peculiar sort of work, some cybercriminals spend a lot of effort to automate it. In March 2018, we came across a fairly simple but effective piece of malware named WinPot. It was created to make...
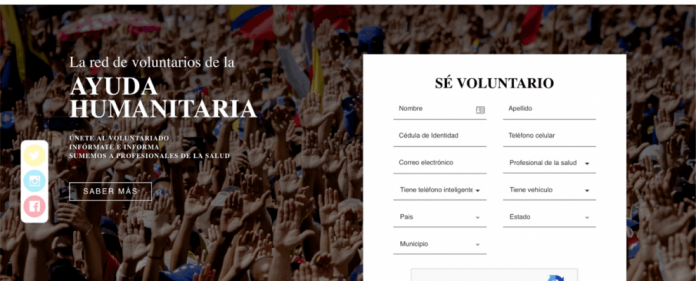
DNS Manipulation in Venezuela in regards to the Humanitarian Aid Campaign
Venezuela is a country facing an uncertain moment in its history. Reports suggests it is in significant need of humanitarian aid.
On February 10th, Mr. Juan Guaidó made a public call asking for volunteers to join a new movement called “Voluntarios por Venezuela” (Volunteers for Venezuela). According to the media, it already numbers thousands of volunteers, willing to help international...
How Imperva’s New Attack Crowdsourcing Secures Your Business’s Applications
Attacks on applications can be divided into two types: targeted attacks and “spray and pray” attacks. Targeted attacks require planning and usually include a reconnaissance phase, where attackers learn all they can about the target organization’s IT stack and application layers. Targeted application attacks are vastly outnumbered by spray and pray attacks. The perpetrators of spray and pray attacks are...
What’s Hiding On Your ICS Network?
What's Hiding On Your ICS Network? #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
DDoS Attacks in Q4 2018
News overview
In Q4 2018, security researchers detected a number of new botnets, which included not only Mirai clones for a change. The fall saw increased activity on the part of the Chalubo bot, whose first attacks were registered in late August. Although the new malware employs snippets of Mirai code and the same persistence techniques as in the Xor.DDoS...