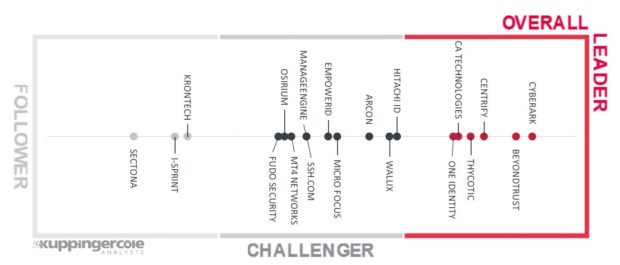
3 for 3! Centrify a Leader in 2019 KuppingerCole Leadership Compass for PAM
KuppingerCole recently published its 2019 KuppingerCole Leadership Compass for Privileged Access Management (PAM), again recognizing Centrify as a Leader as it did in the previous iteration in June 2017.
This marks the third major PAM Market research report in the past 6 months where Centrify was recognized as a Leader, following the same recognition in The Forrester Wave: Privileged Identity...
Operation ShadowHammer: a high-profile supply chain attack
In late March 2019, we briefly highlighted our research on ShadowHammer attacks, a sophisticated supply chain attack involving ASUS Live Update Utility, which was featured in a Kim Zetter article on Motherboard. The topic was also one of the research announcements made at the SAS conference, which took place in Singapore on April 9-10, 2019. Now it is time...
Casino Goes All In and Wins Big with Imperva Security
There’s no good time to be hit by ransom-seeking DDoS attackers. For one casino-entertainment provider, the timing was particularly bad — right before one of its largest online poker events in 2016.
The casino, which generates multiple billions in revenue per year, leveraged Imperva’s emergency onboarding service, allowing us to onboard them to our DDoS Protection service within minutes....
How to Migrate to the Cloud Without Compromising Your Security Posture
How to Migrate to the Cloud Without Compromising Your Security Posture #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0;...
New zero-day vulnerability CVE-2019-0859 in win32k.sys
In March 2019, our automatic Exploit Prevention (EP) systems detected an attempt to exploit a vulnerability in the Microsoft Windows operating system. Further analysis of this event led to us discovering a zero-day vulnerability in win32k.sys. It was the fifth consecutive exploited Local Privilege Escalation vulnerability in Windows that we have discovered in recent months using our technologies. The...
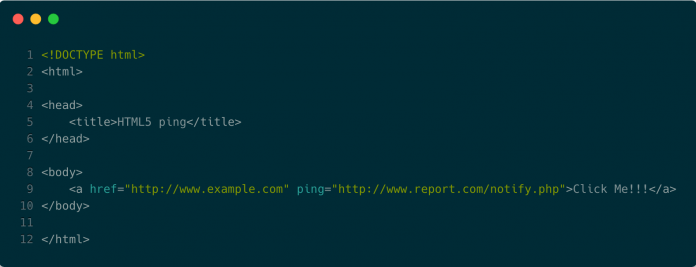
The Ping is the Thing: Popular HTML5 Feature Used to Trick Chinese Mobile Users into Joining Latest DDoS Attack
DDoS attacks have always been a major threat to network infrastructure and web applications.
Attackers are always creating new ways to exploit legitimate services for malicious purposes, forcing us to constantly research DDoS attacks in our CDN to build advanced mitigations.
We recently investigated a DDoS attack which was generated mainly from users in Asia. In this case, attackers...
Large-scale SIM swap fraud
Introduction
SIM swap fraud is a type of account takeover fraud that generally targets a weakness in two-factor authentication and two-step verification, where the second factor or step is an SMS or a call placed to a mobile telephone. The fraud centers around exploiting a mobile phone operator’s ability to seamlessly port a telephone number to a new SIM. This...
Gaza Cybergang Group1, operation SneakyPastes
Gaza Cybergang(s) is a politically motivated Arabic-language cyberthreat actor, actively targeting the MENA (Middle East North Africa) region, especially the Palestinian Territories.
The confusion surrounding Gaza Cybergang’s activities, separation of roles and campaigns has been prevalent in the cyber community. For a while, the gang’s activities seemed scattered, involving different tools and methods, and different malware and infection stages, although...




![[Case Study] Securing Your Data In The Cloud](http://www.dataproof.co.za/wp-content/uploads/2019/04/case-study-securing-your-data-in-the-cloud.jpg)