ScarCruft continues to evolve, introduces Bluetooth harvester
Executive summary
After publishing our initial series of blogposts back in 2016, we have continued to track the ScarCruft threat actor. ScarCruft is a Korean-speaking and allegedly state-sponsored threat actor that usually targets organizations and companies with links to the Korean peninsula. The threat actor is highly skilled and, by all appearances, quite resourceful.
We recently discovered some interesting telemetry on...
Take these Five Steps to Really Mitigate your Data Breach Risks
Data breaches are a CSO/CISO’s worst nightmare. And they’re getting bigger and more damaging all the time. It’s no longer just hundreds of millions of users whose personal data is stolen at a time, but billions of users. That’s translating into ever-growing financial repercussions.
The irony, however, is that companies aren’t investing enough in data security to let them...
The 2019 DBIR is out
Once again, we are happy to support a large, voluntary, collaborative effort like the 2019 Data Breach Investigations Report. While our data contribution is completely anonymous, it is based in some of the 2018 data set that our private report customers receive from our efforts to protect all of our customers against every type of malware threat regardless of...
FIN7.5: the infamous cybercrime rig “FIN7” continues its activities
On August 1, 2018, the US Department of Justice announced that it had arrested several individuals suspected of having ties to the FIN7 cybercrime rig. FIN7 operations are linked to numerous intrusion attempts having targeted hundreds of companies since at least as early as 2015. Interestingly, this threat actor created fake companies in order to hire remote pentesters, developers...
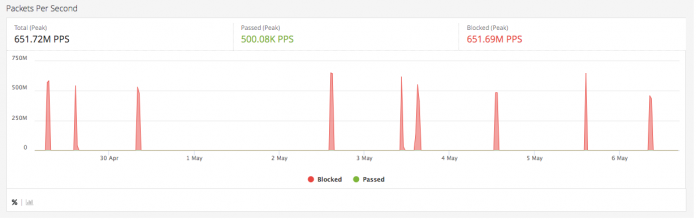
Botnet-led DDoS Attacks Are Hitting Record Intensities. Imperva is Mitigating All of Them.
DDoS attacks are usually ranked by the amount of bandwidth involved, such as the 2018 GitHub attack that peaked at 1.35 Terabits per second and is often cited as the largest DDoS attack ever.
From Imperva’s long history of successfully mitigating DDoS attacks, we know that the TRUE measure of attack intensity is something else — the absolute number of...
Calculating the ROI of a Vulnerability Management Program
Calculating the ROI of a Vulnerability Management Program #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...





![[Buyer’s Guide] DevOps Security](http://www.dataproof.co.za/wp-content/uploads/2019/05/buyers-guide-devops-security.jpg)










