2018 Cyberthreat Defense Report: Where IT Security Is Going
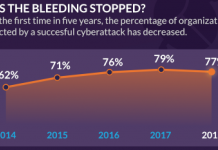
What keeps you awake at night? We asked IT security professionals the same question and found that these issues are top of mind: malware...
How Imperva’s New Attack Crowdsourcing Secures Your Business’s Applications
Attacks on applications can be divided into two types: targeted attacks and “spray and pray” attacks. Targeted attacks require planning and usually include a...
Five Ways Imperva Attack Analytics Helps You Cut Through the Event Noise
The maddening volume of events security teams have to deal with each day is growing at an exponential pace, making it increasingly difficult to effectively...
Enabling Faster DDoS Mitigation for Cloud Assets
The cloud journey was considered a visionary approach less than a decade ago. Today, more than half of organizations rely on a cloud provider,...
Hunting for Insider Threats: Using Activity Modeling to Detect Suspicious Database Commands and Access...
The Widening Gap
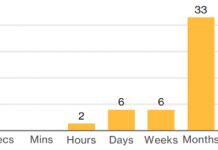
Data breaches by insiders are very challenging to catch. The gap between the rise of insider threats and speed of hunting them...
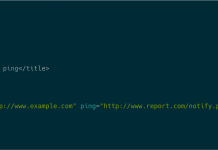
The Ping is the Thing: Popular HTML5 Feature Used to Trick Chinese Mobile Users...
DDoS attacks have always been a major threat to network infrastructure and web applications.
Attackers are always creating new ways to exploit legitimate services...
Women in Tech and Career Spotlight: Jerusalem Bicha
We conclude our series featuring women in tech at Imperva with an interview with Jerusalem Bicha, network operations team lead at Imperva. We talked...
See If You’re GDPR-Ready With Our Last-Minute Checklist
Time’s just about run out to get all your ducks in a row for the EU’s General Data Protection Regulation (GDPR) going into effect...
Imperva Security Update
I want to share details about a security incident at Imperva that resulted in a data exposure impacting our Cloud Web Application Firewall (WAF)...
Every Second Counts When You’re Under Attack — Imperva Provides 3 Second DDoS Mitigation,...
Let’s be blunt: cybersecurity is a never-ending arms race between bad actors and IT and security teams. Lately, attackers have surged. Armed with powerful,...

![Cloud Database Migration Peer Insights [Report]](http://www.dataproof.co.za/wp-content/uploads/2018/01/cloud-database-migration-peer-insights-report-534x462.png)