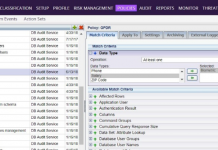
Monitoring Data & Data Access to Support Ongoing GDPR Compliance – Part III: Tools
The new European Union (EU)-wide General Data Protection Regulation (GDPR) was signed into law in late April 2016, and the compliance deadline came into...
RedisWannaMine Unveiled: New Cryptojacking Attack Powered by Redis and NSA Exploits
Recently cryptojacking attacks have been spreading like wildfire. At Imperva we have witnessed it firsthand and even concluded that these attacks hold roughly 90%...
Latest Drupal RCE Flaw Used by Cryptocurrency Miners and Other Attackers
Another remote code execution vulnerability has been revealed in Drupal, the popular open-source Web content management system. One exploit — still working at time...
44% of Security Professionals Spend More than 20 Hours a Week Responding to Alerts
As the global cybersecurity climate continues to heat up, so too do the subsequent levels of alert fatigue IT security professionals have to deal...
Explainer Series: What is Clickjacking?
Here we go, another online trap ready to ensnare unsuspecting – well, until now anyway – users. As if Phishing, Cryptojacking, credential stuffing and...
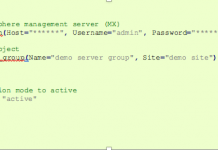
Imperva Python SDK – We’re All Consenting SecOps Here
Managing your WAF can be a complicated task. Custom policies, signatures, application profiles, gateway plugins… there’s a good reason ours is considered the best...
Dynamic Content Acceleration in Imperva CDN Improves Enterprise Website Performance
Today we introduced a new dynamic content acceleration network enhancement feature designed to improve response times to the origin server by up to 30%.
Clients...
How To Leverage Data Access Analytics for Effective Breach Detection
Detecting and preventing data breaches is a challenge for most, if not all, enterprises. In fact, according to a study released in 2017, 78%...
With The NASDAQ Bell Ceremony, We Kick Off The Next Leg of Imperva’s Incredible...
On Friday morning our CEO Chris Hylen and company execs rung the NASDAQ opening bell in New York, welcoming another day of trading for...
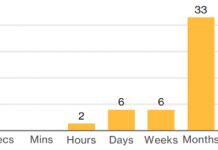
Hunting for Insider Threats: Using Activity Modeling to Detect Suspicious Database Commands and Access...
The Widening Gap
Data breaches by insiders are very challenging to catch. The gap between the rise of insider threats and speed of hunting them...