Imperva to Acquire Distil Networks, the Leader in Advanced Bot Mitigation
As an established leader in cybersecurity, Imperva provides our customers the most comprehensive, analyst-recognized application security solution on the market. We are a five-time...
UK’s Largest Mobile Carrier Relies on AWS and Imperva FlexProtect for Web Delivery and...
In today’s highly-competitive telecommunications market, the website is integral to successful and fast customer service. Downtime due to intrusion, data breach, or DDoS attack...
Explainer Series: RDaaS Security and Managing Compliance Through Database Audit and Monitoring Controls
As organizations move to cloud database platforms they shouldn’t forget that data security and compliance requirements remain an obligation. This article explains how you...
Infonomics-based Model Teaches CISOs how to Assess their Data’s Financial Risk, Invest Properly in...
Here’s what I consider the biggest contradiction in cybersecurity: the most-financially-damaging, reputation-destroying security incidents almost always involves the theft of millions of database records....
Meet the New Imperva – Defending Your Business Growth Today and Tomorrow
Today’s Imperva is a champion in the fight to secure data and applications, wherever they reside. The threat landscape is dangerous and ever-changing, but...
Developers Versus Automation Engineers: How We Ended the Fighting with the Right CI Process
Hey developers and DevOps professionals: what if I told you that how you wrap and execute your automation tests could be the key to...
44% of Security Professionals Spend More than 20 Hours a Week Responding to Alerts
As the global cybersecurity climate continues to heat up, so too do the subsequent levels of alert fatigue IT security professionals have to deal...
New Imperva Java SDK: Greasing The Wheels for Active Directory Coding Projects
According to StackOverflow’s 2018 Developer Survey, Java remains one of the world’s most popular coding languages, universally liked for its versatility and ease of...
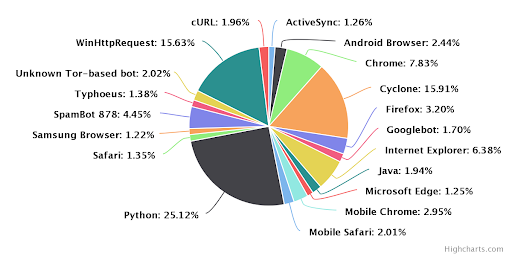
How Account Takeover Botnets Outsmart Traditional Security Controls
Account Takeover (ATO) describes when an online account is accessed and/ or used by someone other than its legitimate owner, usually for malicious purposes....
Stronger Together, Red Hat 3scale Integration
Most enterprises today rely on customers accessing their applications to conduct daily business. These enterprises know by now that application programming interfaces (APIs) are...