Imagine you’re a developer building a new web application. You’ve followed all of the security best practices, hired a reputable penetration testing company before launch, and gone through extensive bug fixing to remove any vulnerabilities. However, would you be confident that your application could survive the largest and longest DDoS attack that you’d ever seen?
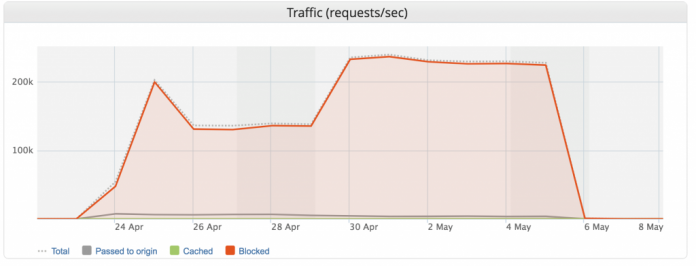
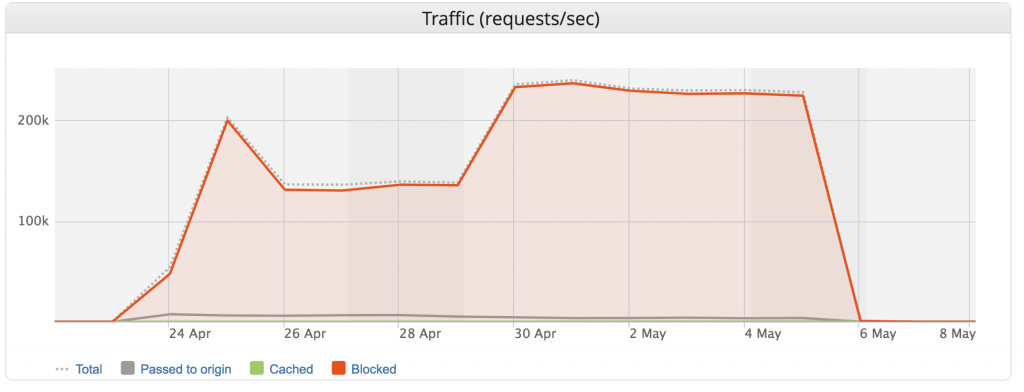
Targeting the authentication component of your site, this DDoS attack was led by a botnet coordinating 402,000 different IPs, lasted 13 days and directed a peak flow of 292,000 RPS (Requests Per Second). Such a massive attack is more than possible — one of our CDN customers in the entertainment industry was hit by one earlier this spring.
It was the largest Layer 7 DDoS attack Imperva has ever seen (see below, click to enlarge). However, our application security successfully mitigated the attack during its entire 13-day span. So despite the ferocity, our customer suffered no downtime.
Imperva has mitigated Layer 3/4 attacks that, using a different measure, peaked at 500 million packets per second. This, however, was the largest DDoS Layer 7 (application layer) attack to date we have observed, using the most relevant measure for Layer 7 attacks, Requests Per Second (You can read more about the types of DDoS here).
Attack Analysis
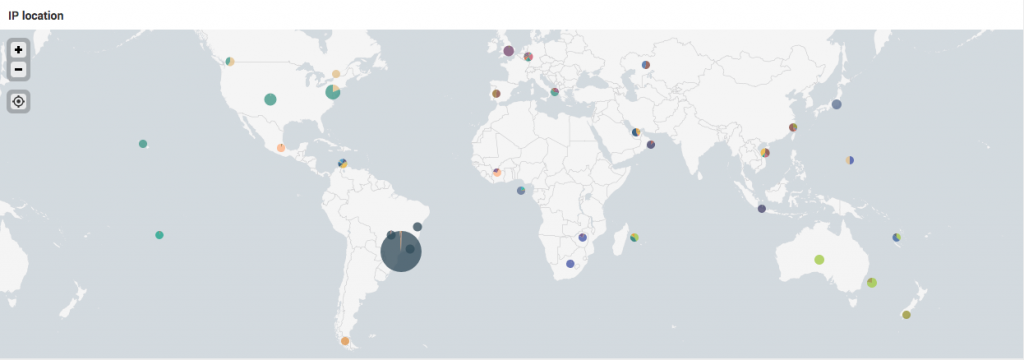
By analyzing the IPs that performed the attack, we found that the main source was Brazil.
 The attackers used a legitimate User-Agent, the same as used by the entertainment industry customer service application, to mask their attack. In spite of this, our client classification mechanism could distinguish it from the customer’s legitimate application.
The attackers used a legitimate User-Agent, the same as used by the entertainment industry customer service application, to mask their attack. In spite of this, our client classification mechanism could distinguish it from the customer’s legitimate application.
For a time, the attack targeted the authentication component of the streaming application. We are not sure if the intent of the attackers was to perform a brute force attack or DDoS attack, but without an accurate mitigation mechanism, the result was the same — denial of service.
Imperva recently released a new capability of our Application Security suite called Account Takeover Protection to protect against advanced account takeover attacks like brute force or credential stuffing. As this attack occurred in late spring before the launch of ATO, we were unable to analyze the brute force aspects of the attack.
So we began looking for a common denominator. We found that most of the IPs had the same opened ports: 2000 and 7547. These are associated with IoT devices infected by the Mirai malware according to the cybersecurity blog, Recorded Future.
Mirai Is Still Alive and Evolving
We analyzed Mirai back in 2016, and published a detailed investigation:“Breaking Down Mirai: An IoT DDoS Botnet Analysis”.
Following the release of Mirai’s source code some years ago, many new variants have emerged. Some of them just included additional IoT device default credentials to target more vendors’ devices, while others added new functionality.
Compromising the IoT device is the first part of the attack. Thereafter, the attacker uploads malicious software to the device that will receive commands from a Command and Control server (CnC). Mirai source code contains only DDoS functionality, but nothing prevents the attacker from including other malicious software to take advantage of compromised devices and perform additional attacks, such as brute force.
Summary
Since 2016, many new IoT vendors have entered the market. Few have learned from the security mistakes of the past. As a result, today IoT devices are used in most of the large botnets we have seen.
Botnets of IoT devices will only get larger. We live in a connected world, so the number of IoT devices continues to grow fast and vendors still do not consider security a top priority.
It is almost impossible to protect your business and your applications from a DDoS attack at this scale without assistance. You need a 3rd party vendor that can handle both Application Layer 7 DDoS attacks and Network Layer 3/4 DDoS attacks.
If we look again at this attack from a brute force (or Account Takeover) perspective, mitigation may seem easy. Can’t you simply limit the rate of authentication attempts on your application?
However, a botnet with 400,000 IPs can perform a “slow and low” attack: each IP tries a few logins, goes inactive, and then tries a few more. In such a technique, the access rate is very low, mimicking legitimate login attempts, and staying under rate limit policies. You can protect yourself, your business and your reputation by using the Account Takeover Protection capability of Imperva’s Application Security stack. Stay safe!
The post Imperva Blocks Our Largest DDoS L7/Brute Force Attack Ever (Peaking at 292,000 RPS) appeared first on Blog.