Achieve CIS Benchmarks for Cloud, Container and DevOps Environments
Achieve CIS Benchmarks for Cloud, Container and DevOps Environments #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100%...
Black Hat 2018
<img src="/sites/default/files/Blackhat-logo.png">
Join Digital Guardian at Black Hat 2018!
- Read more
Making Smarter Access Control Decisions
Hey Siri, block that attacker, please
Wouldn’t it be great if Siri, Alexa, or Google Assistant had the intelligence to figure out malicious intent, govern access to our sensitive corporate data, and alert us in real time when something dodgy was going on? Well, they do leverage modern machine learning and AI to make “intelligent” decisions, but they’re clearly not...
Pbot: evolving adware
The adware PBot (PythonBot) got its name because its core modules are written in Python. It was more than a year ago that we detected the first member of this family. Since then, we have encountered several modifications of the program, one of which went beyond adware by installing and running a hidden miner on victim computers:
Miner code installed...
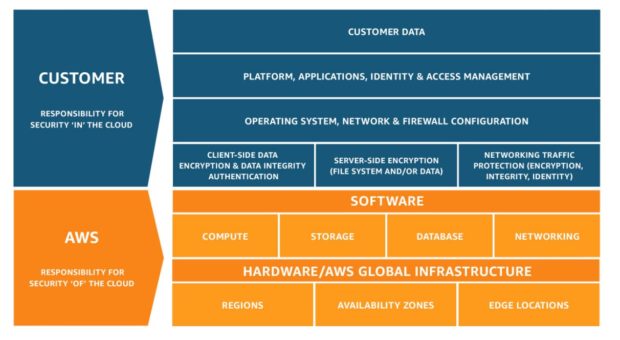
Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018
Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global leaders and IT security practitioners from government, education, and non-profit organizations to learn how to start their path to the cloud or how to maintain momentum once they’ve begun the transformation.
BULLISH OUTLOOK FOR CLOUD ADOPTION...
How To Leverage Data Access Analytics for Effective Breach Detection
Detecting and preventing data breaches is a challenge for most, if not all, enterprises. In fact, according to a study released in 2017, 78% of all CISOs are concerned that data breaches go undetected, while only 19% admit they are effective at breach prevention.
Simply put, breaches happen almost every day; most people know that but have no clue where...
Cyber Risk Insights from the AIG 2017 Cyber Insurance Review
I read with interest AIG’s 2017 Cyber Insurance Review. In a one sentence summary: cyber insurance claims are up, due to systemic ransomware and wiper malware attacks, the cyber business is booming, but we are still early in the market evolution.
Reading the report prompted me to ask three questions regarding Cyber Insurance:
How well do insurance brokers understand cyber risk...