APT Trends Report Q2 2018
In the second quarter of 2017, Kaspersky Lab’s Global Research and Analysis Team (GReAT) began publishing summaries of the quarter’s private threat intelligence reports, in an effort to make the public aware of the research we have been conducting. This report serves as the latest installment, focusing on the relevant activities that we observed during Q2 2018.
These summaries are...
Cloud Security For The Healthcare Industry: A No-Brainer
The healthcare industry has become one of the likeliest to suffer cyber-attacks, and there’s little wonder why. Having the financial and personal information of scores of patients makes it a very appetizing target for attackers.
Just over a year ago, the WannaCry ransomware attack wreaked havoc on the UK National Health Service (NHS), ultimately disrupting a third of its facilities and...
To crypt, or to mine – that is the question
Way back in 2013 our malware analysts spotted the first malicious samples related to the Trojan-Ransom.Win32.Rakhni family. That was the starting point for this long-lived Trojan family, which is still functioning to this day. During that time the malware writers have changed:
the way their Trojans get keys (from locally generated to received from the C&C);
the algorithms used (from using...
A Ticking Time Bomb: Understanding and Securing the Next Generation of Workers
It’s sometimes easy to forget that the younger employees of today are the managers of tomorrow. If we fail to understand how they use technology and perceive security and privacy, it will have a major bearing on the workforce of the future, and the long-term ability of organisations to withstand cyber threats.
To shed some light on the issue, Centrify...
Back to Basics: Let’s Forget About the GDPR… For A Moment
At this point it’s fairly safe to assume that most everyone in the business of “data” has heard of the European Union (EU)-wide General Data Protection Regulation (GDPR) that was signed into law in late April 2016; with the compliance deadline having come into effect on May 25, 2018. Clearly, this new regulation has significant implications for organizations across...
The Complete Guide to Container Security
The Complete Guide to Container Security #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
It’s Time for Managers to Lead Security by Example, Not Blame Younger Workers
The age gap is something that all organisations over the years have had to deal with in one way or another. But the flood of consumer-grade technologies into the workplace in recent years has arguably widened that gap even further.
To learn more, Centrify recently polled not only 1,000 UK office workers aged 18-24 but also 500 senior decision makers....
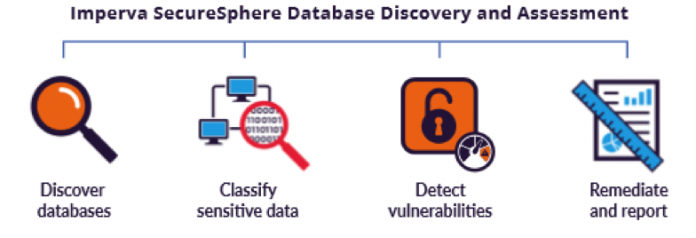
Cloud Migration Fundamentals: Overcoming Barriers to App Security [Infographic]
As more organizations move to the cloud, the line of responsibility in securing applications can become rather blurred.
The concept of control has historically rested in physical location and ownership. With the move to the cloud, however, the idea of security by proxy is changing and so should our approach.
First things first though, how do we meet the challenges that...
Ransomware and malicious crypto miners in 2016-2018
Ransomware is not an unfamiliar threat. For the last few years it has been affecting the world of cybersecurity, infecting and blocking access to various devices or files and requiring users to pay a ransom (usually in Bitcoins or another widely used e-currency), if they want to regain access to their files and devices.
The term ransomware covers two main...







![Cloud Migration Fundamentals: Overcoming Barriers to App Security [Infographic]](https://www.dataproof.co.za/wp-content/uploads/2018/07/cloud-migration-fundamentals-overcoming-barriers-to-app-security-infographic-696x435.png)





