A Bug in Chrome Gives Bad Actors License to Play ‘20 Questions’ with Your Private Data
In a 2013 interview with The Telegraph, Eric Schmidt, then CEO of Google was quoted as saying: “You have to fight for your privacy or lose it.”
Five years later, with the ‘Cambridge Analytica’ data breach scandal fresh in our memory, Eric Schmidt’s statement rings as a self-evident truth. Similarly clear today is the nature of the “fight”: a grapple for transparency...
Watch: An Account Takeover Attack Using Credential Stuffing, and How to Protect Against It [Video]
As cryptocurrencies continue to grow in diversity, so too do the threats they face, specifically those targeting the cryptocurrency exchange. Now, more than ever, cryptocurrency exchanges are facing security threats in the form of volumetric and application layer DDoS and account takeover (ATO) attacks.
Although the success of cryptocurrency exchanges makes them especially attractive to cybercriminals, attacks of late are taking exchanges by...
Learn the essential DevOps practices that today’s most successful organizations are implementing
Learn the essential DevOps practices that today's most successful organizations are implementing #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important;...
Spam and phishing in Q2 2018
Quarterly highlights
GDPR as a phishing opportunity
In the first quarter, we discussed spam designed to exploit GDPR (General Data Protection Regulation), which came into effect on May 25, 2018. Back then spam traffic was limited to invitations to participate in workshops and other educational events and purchase software or databases. We predicted that fraudulent emails were soon to follow. And...
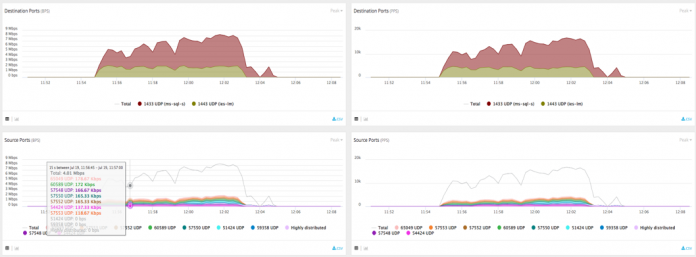
Enhanced Infrastructure DDoS Protection Analytics: Targeted Visibility for Greater Accuracy
We’ve rolled out enhanced infrastructure protection analytics which shows top traffic patterns for traffic flowing through our Incapsula Infrastructure DDoS Protection service.
Imperva clients can now view network statistics categorized by source or destination IPs and ports, or by packet size for protected network ranges. This new addition to our data analytics helps our clients get in-depth visibility into their...
Implementing Modern Approaches to Database Authentication and Authorization
The most common question I hear about Database Accounts is, “Can your solution vault Database Service and other Privileged Database Accounts?”
Every time I hear this question, a voice in the back of my head wants to ask, “Have you implemented modern approaches to Database Authentication and Authorization Management?”
See the real problem is the majority of Databases and the hosted...
CIS Controls and Tripwire Solutions
CIS Controls and Tripwire Solutions #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff;...
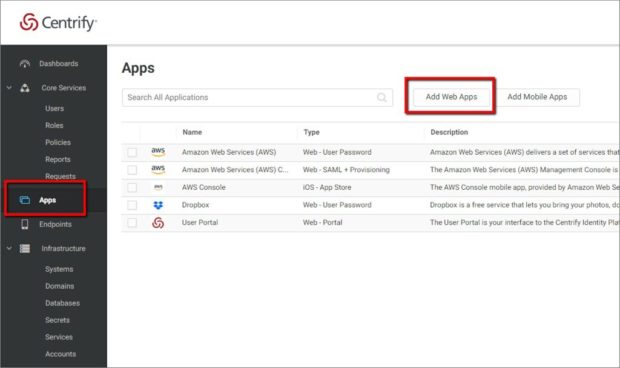
How to Authenticate Users Into Apps Using AWS Application Load Balancer and Centrify
At Centrify, an AWS Partner Network (APN) Advanced Technology Partner, we frequently work with developers building applications on Amazon Web Services (AWS). While many aspects of app development and deployment on AWS have been streamlined, authentication of end-users into apps remains challenging.
A traditional approach is to implement your own identity repository using a relational database or directory server. You are responsible for...