Mastering Container Security: Docker, Kubernetes and More
Mastering Container Security: Docker, Kubernetes and More #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; }...
LuckyMouse signs malicious NDISProxy driver with certificate of Chinese IT company
What happened?
Since March 2018 we have discovered several infections where a previously unknown Trojan was injected into the lsass.exe system process memory. These implants were injected by the digitally signed 32- and 64-bit network filtering driver NDISProxy. Interestingly, this driver is signed with a digital certificate that belongs to Chinese company LeagSoft, a developer of information security software based...
Threat Landscape for Industrial Automation Systems in H1 2018
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and government organizations, banks, telecoms operators, industrial enterprises, and individual users. In this report, Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) publishes the findings of its research on the threat...
Imperva Recognized as a 2018 Gartner Magic Quadrant WAF Leader, Five Years Running
Gartner has named Imperva as a Leader in the 2018 Gartner Magic Quadrant for Web Application Firewalls (WAF) — for the fifth year in a row!
Our combination of on-premises appliances, cloud WAF, shared threat intelligence and flexible licensing once again cement us as the best choice for companies to protect their websites and applications.
Having recently added attack analytics...
Tripwire FIM for Comprehensive Integrity Management
Tripwire FIM for Comprehensive Integrity Management #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
We know what your kids did this summer
For many kids and teenagers, summer is all about ditching school books in favor of hobbies and fun. Every year we release a report on children’s interests, as reflected in their online activity. This summer, we investigated what they prefer in their free time.
The Parental Control module in Kaspersky Lab products protects children from unwanted content, as does the...
What are botnets downloading?
Spam mailshots with links to malware and bots downloading other malware are just a couple of botnet deployment scenarios. The choice of infectious payload is limited only by the imagination of the botnet operator or customer. It might be a ransomware, a banker, a miner, a backdoor, the list goes on, and you don’t need to go far for...
Report: Nearly Half of Security Professionals Think They Could Execute a Successful Insider Attack on Their Organization
As potential threats and entry points into organizations’ databases keep growing, so does the amount of money folks are throwing at detecting and actioning insider threats. In fact, the ballooning amount of money being spent on cybersecurity overall clearly highlights the seriousness with which businesses are tackling the problem in general.
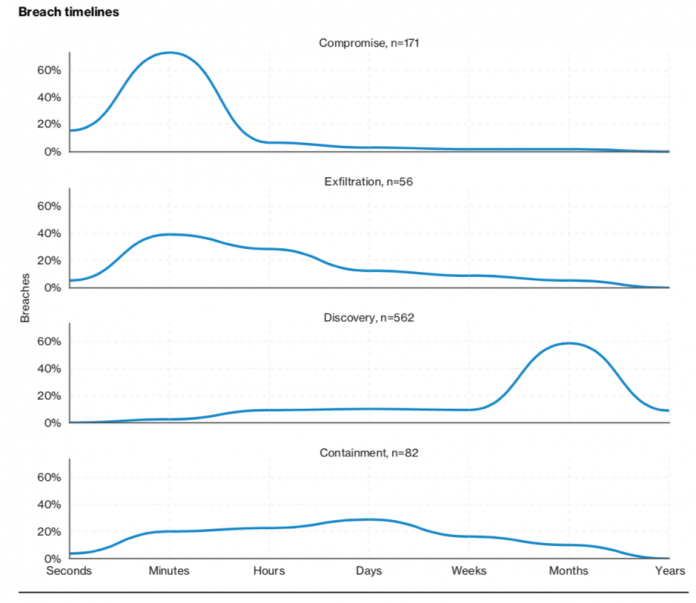
Identifying and containing data breaches
Insider threats are a major...
Loki Bot: On a hunt for corporate passwords
Starting from early July, we have seen malicious spam activity that has targeted corporate mailboxes. The messages discovered so far contain an attachment with an .iso extension that Kaspersky Lab solutions detect as Loki Bot. The malware’s key objective is to steal passwords from browsers, messaging applications, mail and FTP clients, and cryptocurrency wallets. Loki Bot dispatches all its...
Explainer Series: What is Clickjacking?
Here we go, another online trap ready to ensnare unsuspecting – well, until now anyway – users. As if Phishing, Cryptojacking, credential stuffing and old school scamming wasn’t enough, folks really just can’t catch a break these days. Anyway, we’re here to chat about clickjacking, for those of you who aren’t 100% sure what to keep an eye out...