Shedding Skin – Turla’s Fresh Faces
Turla, also known as Venomous Bear, Waterbug, and Uroboros, may be best known for what was at the time an “ultra complex” snake rootkit focused on NATO-related targets, but their malware set and activity is much broader. Our current focus is on more recent and upcoming activity from this APT, which brings an interesting mix of old code, new...
How to Protect Your Critical Assets from Malware
How to Protect Your Critical Assets from Malware #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
Roaming Mantis part III: iOS crypto-mining and spreading via malicious content delivery system
In Q2 2018, Kaspersky Lab published two blogposts about Roaming Mantis sharing details of this new cybercriminal campaign. In the beginning, the criminals used DNS hijacking in vulnerable routers to spread malicious Android applications of Roaming Mantis (aka MoqHao and XLoader), spoofing legitimate applications such as Facebook and Chrome. During our research, it became clear that Roaming Mantis has...
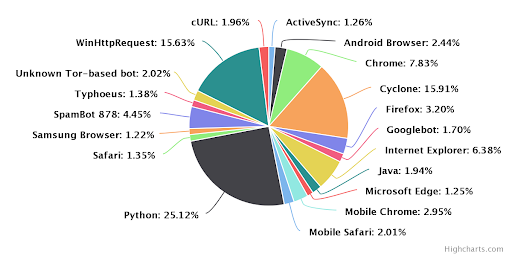
The World’s Most Popular Coding Language Happens to be Most Hackers’ Weapon of Choice
Python will soon be the world’s most prevalent coding language.
That’s quite a statement, but if you look at its simplicity, flexibility and the relative ease with which folks pick it up, it’s not hard to see why The Economist recently touted it as the soon-to-be most used language, globally. Naturally, our threat research team had to poke around...
Five Insights from the Verizon 2018 DBIR
Five Insights from the Verizon 2018 DBIR #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; }...
USB threats from malware to miners
Introduction
In 2016, researchers from the University of Illinois left 297 unlabelled USB flash drives around the university campus to see what would happen. 98% of the dropped drives were picked up by staff and students, and at least half were plugged into a computer in order to view the content. For a hacker trying to infect a computer network,...
Imperva Joins Global Cybersecurity Tech Accord
Imperva is dedicated to the global fight to keep people’s data and applications safe from cybercriminals. What this means for our Imperva Threat Research team is that we spend a lot of time researching new cyber attacks, creating mitigations and writing powerful software. We believe that nothing grows in a vacuum, and as such understand the importance of collaboration...