How would you choose an Industrial Cybersecurity Framework?
How would you choose an Industrial Cybersecurity Framework? #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
Hackers attacking your memories: science fiction or future threat?
Authors: Kaspersky Lab and the Oxford University Functional Neurosurgery Group
There is an episode in the dystopian near-future series Black Mirror about an implanted chip that allows users to record and replay everything they see and hear. A recent YouGov survey found that 29% of viewers would be willing to use the technology if it existed.
If the Black Mirror scenario...
New Imperva Java SDK: Greasing The Wheels for Active Directory Coding Projects
According to StackOverflow’s 2018 Developer Survey, Java remains one of the world’s most popular coding languages, universally liked for its versatility and ease of adoption.
Even so, working under the pressures developers often do, a bit of help always goes a long way. To that end, we’ve put together a shiny new software development kit ( SDK) for Java...
Phishing for knowledge
When we talk about phishing, top of mind are fake banking sites, payment systems, as well as mail and other globally popular services. However, cybercriminals have their fingers in far more pies than that. Unobviously, perhaps, students and university faculties are also in the line of fire. The reason is the research they carry out and the potentially valuable...
Protecting Industrial Operations With Shop-Floor to Top-Floor Visibility
Protecting Industrial Operations With Shop-Floor to Top-Floor Visibility #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
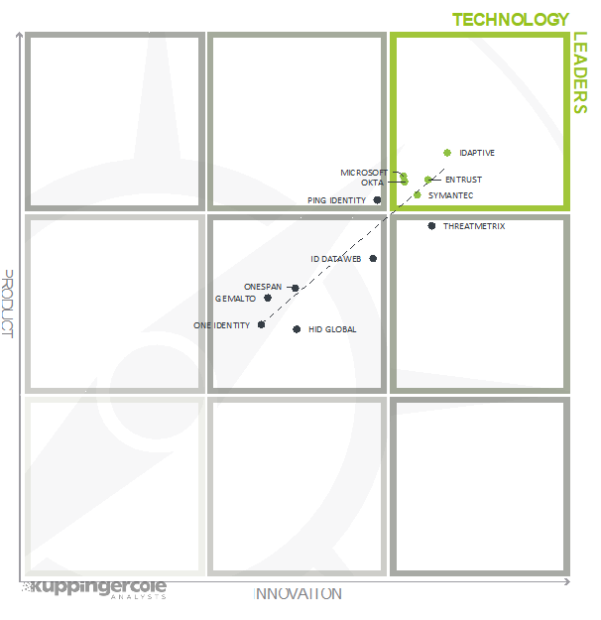
Centrify’s new spinout, Idaptive, named Overall Leader in KuppingerCole Leadership Compass for Cloud-based MFA Solutions
Wow! Right out of the gate and the brand new spinout of Centrify Application and Endpoint Services as Idaptive is named as an Overall Leader in the recent KuppingerCole Leadership Compass for Cloud-based MFA Solutions report. Most organizations today are wrestling with how to better authenticate users. Passwords are not enough and MFA has risen as a secure option...
At SecurIT in New York, it’s a Zero Trust State of Mind
On October 29-30, Centrify will proudly sponsor the second SecurIT: the Zero Trust Summit for CIOs and CISOs in New York City. Produced by CIO and CSO from IDG in partnership with Centrify, the two-day event will focus on how to capitalize on the adoption wave of Zero Trust to stay ahead of the security curve.
The summit will be...
44% of Security Professionals Spend More than 20 Hours a Week Responding to Alerts
As the global cybersecurity climate continues to heat up, so too do the subsequent levels of alert fatigue IT security professionals have to deal with.
A recent survey by Imperva reveals that nine percent of UK security teams battle with over five million alerts each week. Five million, just let that sink in for a minute.
We spoke to 185 security...
Survey: 44% of Security Professionals Spend More than 20 Hours a Week Responding to Alerts
As the global cybersecurity climate continues to heat up, so too do the subsequent levels of alert fatigue IT security professionals have to deal with.
A recent survey by Imperva reveals that nine percent of UK security teams battle with over five million alerts each week. Five million, just let that sink in for a minute.
We spoke to 185 security...