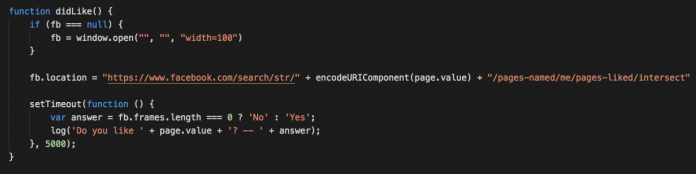
Patched Facebook Vulnerability Could Have Exposed Private Information About You and Your Friends
In a previous blog we highlighted a vulnerability in Chrome that allowed bad actors to steal Facebook users’ personal information; and, while digging around for bugs, thought it prudent to see if there were any more loopholes that bad actors might be able to exploit.
What popped up was a bug that could have allowed other websites to extract private...
New Docker-based Dev Pipeline: Microservice Projects Just Got A ‘Speed-Boost’
A bulwark of software engineering projects, the development pipeline is an automated process used to deliver changes from development through to production; enabling near real-time updates.
The dev pipeline is a critical time saver as it enables you to:
Avoid mistakes (and wasted time as a result) through automation.
Supply quick feedback for any changes in the software (good or bad).
Operate...
The Base of Cyber-Attacks: Credential Harvesting
Cyber attackers long ago figured out that the easiest way to gain access to sensitive data is by compromising an end user’s identity and credentials. According to the Verizon 2017 Data Breach Investigation Report, 81% of hacking-related breaches leverage either stolen, default, or weak credentials. Often these credentials belong to privileged users, providing cyber adversaries the “keys to the...
The Dos and Don’ts of DevOps
The Dos and Don'ts of DevOps #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
Spam and phishing in Q3 2018
Quarterly highlights
Personal data in spam
We have often said that personal data is candy on a stick to fraudsters and must be kept safe (that is, not given out on dubious websites). It can be used to gain access to accounts and in targeted attacks and ransomware campaigns.
In Q3, we registered a surge of fraudulent emails in spam traffic. This...
Hey there! How much are you worth?
Have you ever stopped to think just how much your life is worth? I mean really think about it. For instance, let’s say you wanted to sell everything you have – your house, your car, your job, your private life, photos and home movies from your childhood, your accounts on various social media, your medical history and so on...
DDoS Attacks in Q3 2018
News Overview
The third quarter 2018 turned out relatively quiet in terms of DDoS attacks. “Relatively” because there were not very many high-level multi-day DDoS onslaughts on major resources. However, the capacities employed by cybercriminals keep growing year after year, while the total number of attacks shows no signs of decline.
The early July attack on Blizzard Entertainment has made some...