DNS Manipulation in Venezuela in regards to the Humanitarian Aid Campaign
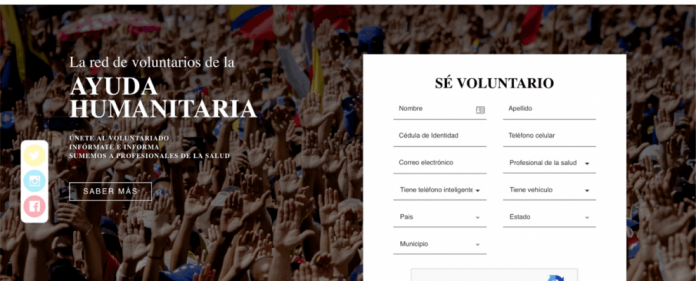
Venezuela is a country facing an uncertain moment in its history. Reports suggests it is in significant need of humanitarian aid.
On February 10th, Mr. Juan Guaidó made a public call asking for volunteers to join a new movement called “Voluntarios por Venezuela” (Volunteers for Venezuela). According to the media, it already numbers thousands of volunteers, willing to help international...
How Imperva’s New Attack Crowdsourcing Secures Your Business’s Applications
Attacks on applications can be divided into two types: targeted attacks and “spray and pray” attacks. Targeted attacks require planning and usually include a reconnaissance phase, where attackers learn all they can about the target organization’s IT stack and application layers. Targeted application attacks are vastly outnumbered by spray and pray attacks. The perpetrators of spray and pray attacks are...
What’s Hiding On Your ICS Network?
What's Hiding On Your ICS Network? #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
DDoS Attacks in Q4 2018
News overview
In Q4 2018, security researchers detected a number of new botnets, which included not only Mirai clones for a change. The fall saw increased activity on the part of the Chalubo bot, whose first attacks were registered in late August. Although the new malware employs snippets of Mirai code and the same persistence techniques as in the Xor.DDoS...
Five Reasons to Visit Centrify Booth #N6445 at RSA 2019
The 2019 RSA Conference is just around the corner, coming up March 4-8 at the Moscone Center in San Francisco!
If you’ve never attended an RSA show before, this is the security event of the year and the best opportunity you’ll find to network with over 40,000 other security professionals — exchanging ideas, learning the latest trends and finding solutions that empower...
Report: The State of Container Security
Report: The State of Container Security #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
A Cybersecurity and Cloud Innovator – and a Great Partner
Imperva has long been a cybersecurity leader, recognized by the likes of Gartner and Forrester Research for the capabilities of our application and data Security solutions. For more than 6,000 business customers, we are their champion in the daily fight to secure data and applications.
To ensure that we are doing our absolute best to protect our customer’s business, we...
The Challenges of DIY Botnet Detection – and How to Overcome Them
Botnets have been around for over two decades, and with the rise of the Internet of Things (IoT) they have spread further to devices no one imagined they would – printers, webcams, and even toasters and fridges.
Some botnets enlist infected devices to mine cryptocurrency or steal passwords from other devices. But others are, in fact, legions of bot-soldiers waiting...