Mapping Communication Between Facebook Accounts Using a Browser-Based Side Channel Attack
A now-patched vulnerability in the web version of Facebook Messenger allowed any website to expose who you have been messaging with.
In a previous post, I showed how your Facebook likes, location history, and other metadata could have been extracted from your Facebook account using a side-channel attack I named “Cross-Site Frame Leakage,” or CSFL for short.
In this post, I’ll...
Financial Cyberthreats in 2018
Introduction and Key Findings
The world of finance has been a great source of income cybercriminals across the world due to an obvious reason – money. While governments and organizations have been investing in new methods to protect financial services, malicious users have been investing in how to bypass them. This has fueled many changes in how online financial services...
Time to Retire “The Year Of…” at RSA 2019
Today at the RSA Security Conference, we announced Centrify’s Cloud-Ready Zero Trust Privilege Services architecture, including a wide range of enhancements that redefine legacy Privileged Access Management (PAM). If you are at the show, we hope you pay us a visit in Booth 6445 where we can demo a range of DevOps, Automation, hybrid cloud, and infrastructure security protections...
Case Study: Keeping the Lights On with NERC CIP Compliance from Tripwire
Case Study: Keeping the Lights On with NERC CIP Compliance from Tripwire #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important;...
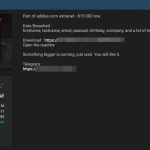
Hundreds of Vulnerable Docker Hosts Exploited by Cryptocurrency Miners
Docker is a technology that allows you to perform operating system level virtualization. An incredible number of companies and production hosts are running Docker to develop, deploy and run applications inside containers.
You can interact with Docker via the terminal and also via remote API. The Docker remote API is a great way to control your remote Docker host,...
Centrify RSA Booth 6445: Where Zero Trust Privilege Partners Take the Stage
If there was one clear takeaway from the 2018 RSA Conference, it was that Zero Trust was ready to take off.
It seemed like everywhere you turned, Zero Trust was staring you in the face. Oh wait, that was just the Centrify marketing blitz that overtook San Francisco and Moscone Center last April!
ZERO TRUST, 10 MONTHS LATER
Fast-forward 10 months ahead...
Don’t Let Security Needs Halt Your Digital Transformation. Imperva FlexProtect Offers Agile Security for any Enterprise.
Is your enterprise in the midst of a digital transformation? Of course it is. Doing business in today’s global marketplace is more competitive than ever. Automating your business processes and infusing them with always-on, real-time applications and other cutting-edge technology is key to keeping your customers happy, attracting and retaining good workers, transacting with your partners, and growing your...


![[Case Study] Preventing Information Security Silos](https://www.dataproof.co.za/wp-content/uploads/2019/03/case-study-preventing-information-security-silos.jpg)