Roaming Mantis, part IV
One year has passed since we published the first blogpost about the Roaming Mantis campaign on securelist.com, and this February we detected new activities by the group. This blogpost is follow up on our earlier reporting about the group with updates on their tools and tactics.
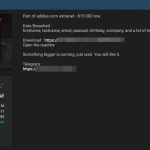
Mobile config for Apple phishing
Our key finding is that the actor continues to seek...
Not just for Processing: How Kafka Streams as a Distributed Database Boosted our Reliability and Reduced Maintenance
The Apache Kafka Streams library is used by enterprises around the world to perform distributed stream processing on top of Apache Kafka. One aspect of this framework that is less talked about is its ability to store local state, derived from stream processing.
In this blog post we describe how we took advantage of this ability in Imperva’s Cloud...
Centrify Empowers Our Partners to Unleash P.E.A.K. Performance
I’m thrilled today to debut Centrify P.E.A.K. Performance, our new partner program!
This launch is the culmination of a long period of listening. We’ve spent months listening to our partners, customers, and internal stakeholders to construct a program from the ground up that we feel empowers the channel to successfully sell Centrify’s cloud-based Zero Trust Privilege services.
First, a step back....
Imperva Wins CRN 5-Star Partner Program 3rd Year in a Row. Here are Some Stats Behind Why.
A lot goes into building a good IT channel program. A truly-effective program should meet the vendor’s needs while also delivering attractive benefits to our partners.
A successful channel program should deliver a number of key elements, including:
partner profitability
partner self-service access to tools and training to help them effectively sell and service customers
demand creation tools
partner access to formal...
Bots and botnets in 2018
Due to the wide media coverage of incidents involving Mirai and other specialized botnets, their activities have become largely associated with DDoS attacks. Yet this is merely the tip of the iceberg, and botnets are used widely not only to carry out DDoS attacks, but to steal various user information, including financial data. The attack scenario usually looks as...
Enhance Imperva Cloud WAF with a New Management Tool in the Imperva GitHub
Imperva recently launched the Imperva GitHub where our global community can access tools, code repositories and other neat resources that aid collaboration and streamline development.
The nice thing about these tools is that you can clone them and customize them with whatever functionality you need. If you are nice you can also push new capabilities and even bug fixes...
Threat Landscape for Industrial Automation Systems in H2 2018
H2 2018 in figures
All statistical data used in this report was collected using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers. We do not identify the specific companies/organizations sending statistics to KSN, due to the product limitations and...
AZORult++: Rewriting history
The AZORult Trojan is one of the most commonly bought and sold stealers in Russian forums. Despite the relatively high price tag ($100), buyers like AZORult for its broad functionality (for example, the use of .bit domains as C&C servers to ensure owner anonymity and to make it difficult to block the C&C server), as well as its high...
Imperva Cloud WAF and Graylog, Part II: How to Collect and Ingest SIEM Logs
This guide gives step-by-step guidance on how to collect and parse Imperva Cloud Web Application Firewall (WAF, formerly Incapsula) logs into the Graylog SIEM tool. Read Part I to learn how to set up a Graylog server in AWS and integrate with Imperva Cloud WAF.
This guide assumes:
You have a clean Graylog server up and running, as described in...