How to Migrate to the Cloud Without Compromising Your Security Posture
How to Migrate to the Cloud Without Compromising Your Security Posture #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0;...
New zero-day vulnerability CVE-2019-0859 in win32k.sys
In March 2019, our automatic Exploit Prevention (EP) systems detected an attempt to exploit a vulnerability in the Microsoft Windows operating system. Further analysis of this event led to us discovering a zero-day vulnerability in win32k.sys. It was the fifth consecutive exploited Local Privilege Escalation vulnerability in Windows that we have discovered in recent months using our technologies. The...
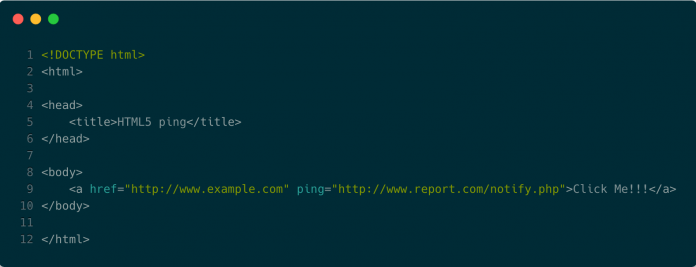
The Ping is the Thing: Popular HTML5 Feature Used to Trick Chinese Mobile Users into Joining Latest DDoS Attack
DDoS attacks have always been a major threat to network infrastructure and web applications.
Attackers are always creating new ways to exploit legitimate services for malicious purposes, forcing us to constantly research DDoS attacks in our CDN to build advanced mitigations.
We recently investigated a DDoS attack which was generated mainly from users in Asia. In this case, attackers...
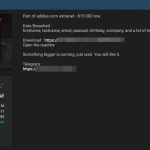
Large-scale SIM swap fraud
Introduction
SIM swap fraud is a type of account takeover fraud that generally targets a weakness in two-factor authentication and two-step verification, where the second factor or step is an SMS or a call placed to a mobile telephone. The fraud centers around exploiting a mobile phone operator’s ability to seamlessly port a telephone number to a new SIM. This...
Gaza Cybergang Group1, operation SneakyPastes
Gaza Cybergang(s) is a politically motivated Arabic-language cyberthreat actor, actively targeting the MENA (Middle East North Africa) region, especially the Palestinian Territories.
The confusion surrounding Gaza Cybergang’s activities, separation of roles and campaigns has been prevalent in the cyber community. For a while, the gang’s activities seemed scattered, involving different tools and methods, and different malware and infection stages, although...
Project TajMahal – a sophisticated new APT framework
Executive summary
‘TajMahal’ is a previously unknown and technically sophisticated APT framework discovered by Kaspersky Lab in the autumn of 2018. This full-blown spying framework consists of two packages named ‘Tokyo’ and ‘Yokohama’. It includes backdoors, loaders, orchestrators, C2 communicators, audio recorders, keyloggers, screen and webcam grabbers, documents and cryptography key stealers, and even its own file indexer for the...
The Industrial Control System Visibility Imperative
The Industrial Control System Visibility Imperative #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
Making Our Security Portfolio Simpler — and Better
Since its inception in 2009, Incapsula has been a proud part of Imperva, the analyst-recognized cybersecurity leader.
However, cybersecurity needs are evolving, and so are we.
On April 7th, we will officially retire Incapsula.com. All of the great Incapsula web site content that wasn’t already migrated to Imperva.com will move on that date. You can continue to access Incapsula...
BasBanke: Trend-setting Brazilian banking Trojan
BasBanke is a new Android malware family targeting Brazilian users. It is a banking Trojan built to steal financial data such as credentials and credit/debit card numbers, but not limited to this functionality. The propagation of this threat began during the 2018 Brazilian elections, registering over 10,000 installations to April 2019 from the official Google Play Store alone.
This malware...



![[Case Study] Securing Your Data In The Cloud](https://www.dataproof.co.za/wp-content/uploads/2019/04/case-study-securing-your-data-in-the-cloud.jpg)