The 2019 DBIR is out
Once again, we are happy to support a large, voluntary, collaborative effort like the 2019 Data Breach Investigations Report. While our data contribution is completely anonymous, it is based in some of the 2018 data set that our private report customers receive from our efforts to protect all of our customers against every type of malware threat regardless of...
FIN7.5: the infamous cybercrime rig “FIN7” continues its activities
On August 1, 2018, the US Department of Justice announced that it had arrested several individuals suspected of having ties to the FIN7 cybercrime rig. FIN7 operations are linked to numerous intrusion attempts having targeted hundreds of companies since at least as early as 2015. Interestingly, this threat actor created fake companies in order to hire remote pentesters, developers...
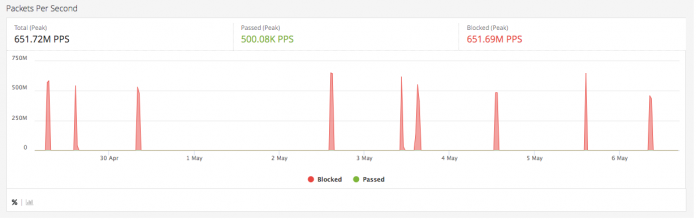
Botnet-led DDoS Attacks Are Hitting Record Intensities. Imperva is Mitigating All of Them.
DDoS attacks are usually ranked by the amount of bandwidth involved, such as the 2018 GitHub attack that peaked at 1.35 Terabits per second and is often cited as the largest DDoS attack ever.
From Imperva’s long history of successfully mitigating DDoS attacks, we know that the TRUE measure of attack intensity is something else — the absolute number of...
Calculating the ROI of a Vulnerability Management Program
Calculating the ROI of a Vulnerability Management Program #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
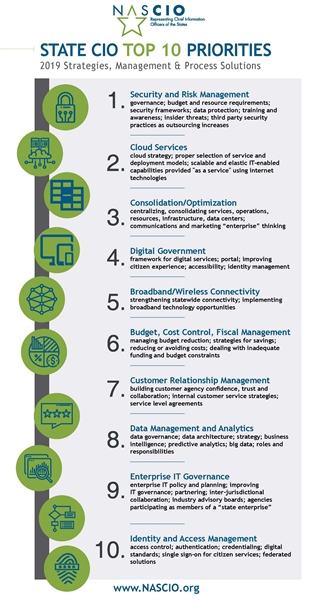
NASCIO CIO Top Priorities in a Zero Trust World
Many state CIOs are struggling to manage the onslaught of priorities that are captured in the NASCIO Top 10 Policy and Technology Priorities for 2019, ranging from enabling cloud services to the digital government to IT governance. While their mission mandates tackling these priorities, they cannot solely focus on their implementation, but must also bolster cyber security and abide...
Building a Mature Vulnerability Management Program
Building a Mature Vulnerability Management Program #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
APT trends report Q1 2019
For just under two years, the Global Research and Analysis Team (GReAT) at Kaspersky Lab has been publishing quarterly summaries of advanced persistent threat (APT) activity. The summaries are based on our threat intelligence research and provide a representative snapshot of what we have published and discussed in greater detail in our private APT reports. They aim to highlight...
I know what you did last summer, MuddyWater blending in the crowd
Introduction
MuddyWater is an APT with a focus on governmental and telco targets in the Middle East (Iraq, Saudi Arabia, Bahrain, Jordan, Turkey and Lebanon) and also a few other countries in nearby regions (Azerbaijan, Pakistan and Afghanistan).
MuddyWater first surfaced in 2017 and has been active continuously, targeting a large number of organizations. First stage infections and graphical decoys have...




![[Buyer’s Guide] DevOps Security](https://www.dataproof.co.za/wp-content/uploads/2019/05/buyers-guide-devops-security.jpg)