Hunting for Insider Threats: Using Activity Modeling to Detect Suspicious Database Commands and Access Patterns
The Widening Gap
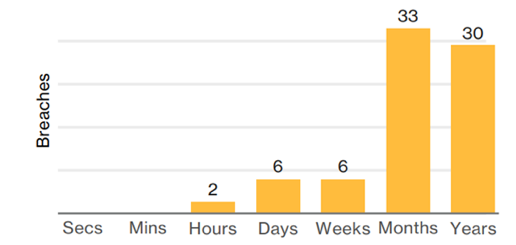
Data breaches by insiders are very challenging to catch. The gap between the rise of insider threats and speed of hunting them down is increasingly widening. According to 2017 Data Breach Investigation Report by Verizon, a great majority of insider and privileged-misuse breaches go undetected months or even years (Figure 1). To make matters worse, it has...
With Less Than 100 Days to Go, How to Get C-Level Buy-in for GDPR Compliance
For GDPR compliance initiatives to work effectively, there has to be buy-in from the boardroom. That doesn’t just mean releasing the necessary funds to bolster efforts ahead of 25 May, but understanding the need for long-term cultural and process changes to the organisation in the years to follow.
However, with less than 100 days to go until the compliance deadline,...
Another Ransomware Variant Strikes Colorado DOT Days after Initial Attack
Posts from The State of Security for 03/02/2018
Inside a New DDoS Amplification Attack Vector via Memcached Servers
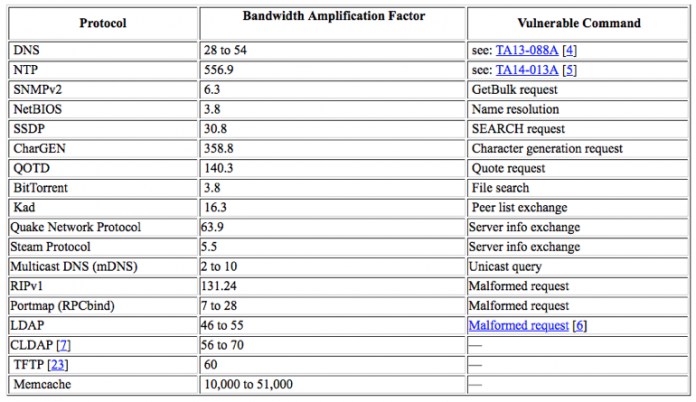
We recently saw a new DDoS amplification attack vector via memcached servers that culminated in two massive DDoS amplification attacks on February 28. Both attacks were mitigated successfully.
Here’s how memchached servers work and how the attacks unfolded.
Memcached servers
Unless updated within the last two days, memcached servers listen on UDP port 11211 by default. This can be exploited to produce...
Takeaways from the Russia-Linked US Senate Phishing Attacks
The Zero Trust Security approach could empower organizations and protect their customers in ways that go far beyond typical security concerns.
On January 12, 2018, cybersecurity firm Trend Micro revealed that Russia-linked hackers tried to infiltrate the US Senate, leveraging phishing attacks to harvest access credentials. These tactics suggest that the hackers were laying the groundwork for a widespread compromise of Senate...
Financial Cyberthreats in 2017
In 2017, we saw a number of changes to the world of financial threats and new actors emerging. As we have previously noted, fraud attacks in financial services have become increasingly account-centric. User data is a key enabler for large-scale fraud attacks, and frequent data breaches – among other successful attack types – have provided cybercriminals with valuable sources...
IoT hack: how to break a smart home… again
There can never be too many IoT gadgets – that’s what people usually think when buying yet another connected device with advanced functionality. From our perspective, we also think there can’t be too many IoT investigations. So, we have continued our experiments into checking and uncovering how vulnerable they are, and followed up our research focusing on smart home...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming into a trusted method for preventing misuse. Experts have consistently stated that enterprises need to implement protections at vulnerable points and apply effective access security mechanisms such as MFA. So, what’s the deal? The Deloitte...
Subscribe to Data Insider
Subscribe to <span style="color: #11111; font-style: bold; letter-spacing: -1px;">DATA</span><span style="color: #E51892; font-style: italic; font-style: bold; letter-spacing: -1px;">INSIDER</span>
.blog_subscribe_block{ margin-top: 50px !important; margin-left: auto; margin-right: auto; margin-bottom: 50px;
}
Want to keep up with the latest from Data Insider? Subscribe to get daily or weekly email updates and make sure you don’t miss an article.
Take me to Data Insider
...
NEW: Vulnerability and Assessment Scanning for Your AWS Cloud Databases
Scuba is a free and easy-to-use tool that uncovers hidden security risks. Scuba is frequently updated with content from Imperva’s Defense Center researchers.
With Scuba you can:
Scan enterprise databases for vulnerabilities and misconfigurations
Identify risks to your databases
Get recommendations on how to mitigate identified issues
Available for Windows, Mac, and Linux, Scuba offers over 2,300 assessment tests for Oracle, Microsoft SQL, SAP...