Somebody’s watching! When cameras are more than just ‘smart’
Every year the number of smart devices grows. Coffee machines, bracelets, fridges, cars and loads of other useful gadgets have now gone smart. We are now seeing the emergence of smart streets, roads and even cities.
Devices such as smart cameras have long been part of everyday life for many, as communication devices, components in security and video surveillance systems,...
Masha and these Bears
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a prolific, well resourced, and persistent adversary. They are sometimes portrayed as wild and reckless, but as seen under our visibility, the group can be pragmatic, measured, and agile. Our previous post on their 2017 activity stepped away from the previously covered headline buzz presenting their association with...
The Slingshot APT FAQ
While analysing an incident which involved a suspected keylogger, we identified a malicious library able to interact with a virtual file system, which is usually the sign of an advanced APT actor. This turned out to be a malicious loader internally named ‘Slingshot’, part of a new, and highly sophisticated attack platform that rivals Project Sauron and Regin in...
RedisWannaMine Unveiled: New Cryptojacking Attack Powered by Redis and NSA Exploits
Recently cryptojacking attacks have been spreading like wildfire. At Imperva we have witnessed it firsthand and even concluded that these attacks hold roughly 90% of all remote code execution attacks in web applications.
Having said that, all of the attacks we have seen so far, were somewhat limited in their complexity and capability. The attacks contained malicious code that downloaded...
The devil’s in the Rich header
In our previous blog, we detailed our findings on the attack against the Pyeongchang 2018 Winter Olympics. For this investigation, our analysts were provided with administrative access to one of the affected servers, located in a hotel based in Pyeongchang county, South Korea. In addition, we collected all available evidence from various private and public sources and worked with...
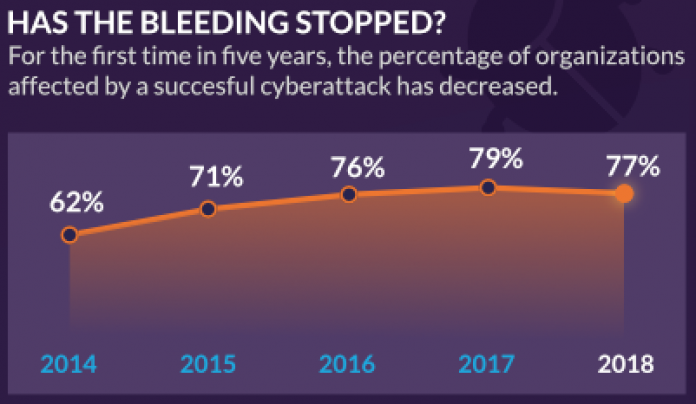
2018 Cyberthreat Defense Report: Where IT Security Is Going
What keeps you awake at night? We asked IT security professionals the same question and found that these issues are top of mind: malware and spear phishing, securing mobile devices, employee security awareness and new technologies that detect threats capable of bypassing traditional signature-based defenses.
In previous years cyberattacks were on a steady and alarming rise. But now, data shows...
Frost & Sullivan Recognizes Centrify for IDaaS and PIM Leadership
Today Frost & Sullivan, a leading analyst firm and growth partnership company, announced that Centrify has earned the North American Product Leadership Award for its Next-Gen Access Solution for Zero Trust Security. The report specifically noted Centrify’s success as a security company comes by challenging traditional approaches to security and using a unique philosophy to address the problem. Centrify...
Protecting Your Organization from the Next Big Ransomware Threat
Protecting Your Organization from the Next Big Ransomware Threat #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100%...
Welcome to The State of Security
Welcome to The State of Security #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...