DevOps-Ready WAF: Scaling Security for a More Agile Environment
With the maturation of DevOps, the growing concern around the security and compliance of more agile application development systems has made 2018 the year for DevSecOps. According to a study by Gartner, over 80% of development teams will have embedded DevSecOps by 2021. When evaluating how a WAF solution can fit in to a DevSecOps model, it’s important to...
GDPR and Privacy: How to Earn the Trust of Your Customers and Keep Regulators Happy
Customer data is the lifeblood of any organisation and the key to unlocking sales and growth. But the data you hold and how you use it is about to come under intense scrutiny, thanks to new European privacy rules.
The EU General Data Protection Regulation (GDPR) is the biggest shake-up to the region’s laws in this area in almost a...
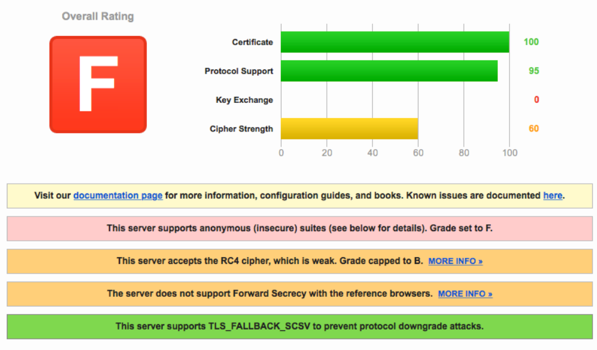
Making the Grade: Achieve SSL Labs A+ Grade with Imperva WAF
We all woke up to a new reality early last year. HTTPS adoption has reached the tipping point, meaning that more than half of web traffic is encrypted.
The benefits of encrypting your traffic are obvious, right? It’s essentially about you securing data being transmitted by authenticating web servers and clients (web browsers), and then using it to encrypt messages...
Your new friend, KLara
While doing threat research, teams need a lot of tools and systems to aid their hunting efforts – from systems storing Passive DNS data and automated malware classification to systems allowing researchers to pattern-match a large volume of data in a relatively short period of time. These tools are extremely useful when working on APT campaigns where research is...
18 Expert Tips for Effective and Secure Cloud Migration
18 Expert Tips for Effective and Secure Cloud Migration #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100%...
Real-Life Exposed Privileged Identity Theft
Have you ever had your identity stolen? Credit cards obtained under your name that were not yours?
Most of us have, and what a pain it can be to stop excess charges, get reimbursed, close down those accounts, and repair your damaged credit. It can take years to recover from such an invasion.
While we know what it’s like in our...
Threat Landscape for Industrial Automation Systems in H2 2017
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and government organizations, banks, telecoms operators, industrial enterprises, and individual users. In this report, Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) publishes the findings of its research on the threat...
Q4 2017 Global DDoS Threat Landscape Report
Today we are releasing our latest Global DDoS Threat Landscape Report, a statistical analysis of 5,055 network and application layer DDoS attacks mitigated by Imperva Incapsula services during Q4 2017.
In Q4, the number of application layer attacks nearly doubled, just as the number of network layer assaults declined. In both cases, however, we saw attacks grow more persistent.
Target wise,...
Six Reasons to Experience Zero Trust Security in Centrify Booth 501 at RSA
In case you hadn’t heard, the 2018 RSA Conference will be held April 16-19 at the Moscone Center in San Francisco. If you haven’t been, this is the security event of the season and the best opportunity you’ll find to network with 50,000 other security professionals — exchanging ideas, learning the latest trends and finding solutions that empower you...